包阅导读总结
1.
关键词:Entra ID、Azure DevOps、Databricks、CI/CD、安全
2.
总结:本文介绍了在 CI/CD 中为增强安全性,整合 Entra ID、Azure DevOps 和 Databricks 的方法,包括创建服务主体、授予权限、使用 CLI 创建和存储 Entra ID 令牌作为 Git 凭据,强调了其相较于 PAT 令牌的优势及后续的安全措施。
3.
主要内容:
– 介绍使用 PAT 令牌访问服务的便捷性及缺点,如不能为服务主体和托管身份发布、最大寿命长等。
– 提出使用 Microsoft Entra ID 访问令牌作为更安全的替代方案,因其每小时过期。
– 详细说明整合流程的前提条件及步骤:
– 前提条件是创建服务主体。
– 步骤包括在 Azure DevOps 项目中授予服务主体读者权限,在 Databricks 中授予服务主体所需权限,使用 CLI 创建 Entra ID 令牌并存储在 Databricks Git 凭据中。
– 总结此流程已学会用 Entra ID 令牌替代 PAT 令牌作为凭据,提及在生产环境中还需额外安全措施,如将秘密存储在 Azure Key Vault 中。
思维导图: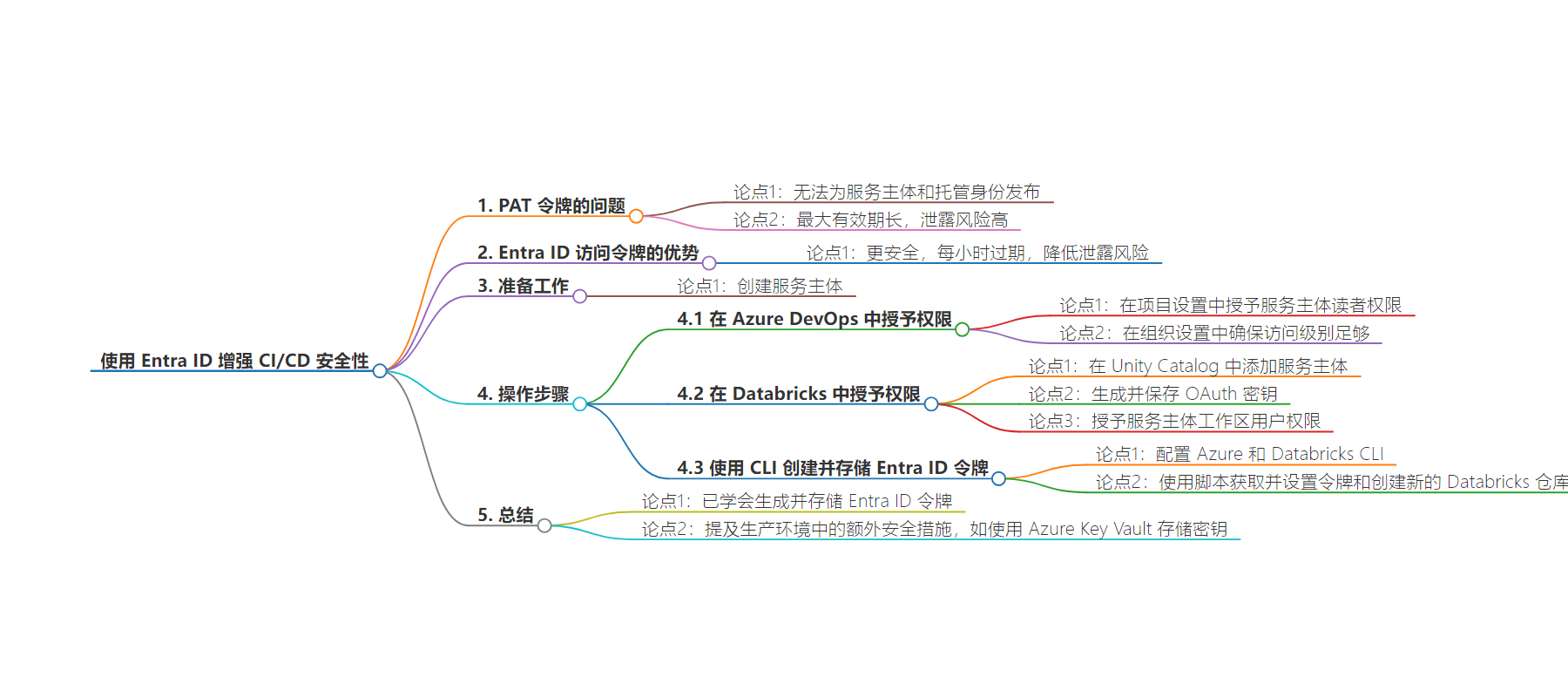
文章来源:databricks.com
作者:Databricks
发布时间:2024/9/11 15:45
语言:英文
总字数:940字
预计阅读时间:4分钟
评分:81分
标签:CI/CD,安全,Azure DevOps,Databricks,Microsoft Entra ID
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Personal Access Tokens (PATs) are a convenient way to access services like Azure Databricks or Azure DevOps without logging in with your password.Today, many customers use Azure DevOps PAT tokens as Git credentials for remote repositories in Databricks Git folders (formerly Repos).Unfortunately, the use of PAT tokens comes with some downsides.In Azure DevOps, PAT tokens cannot be issued to service principals and managed identities, which means that customers resort to a service account or even a user’s identity.Additionally, the maximum lifespan of PAT tokens is often days, weeks, or even months. While their rotation (the process of refreshing the tokens such that older ones can no longer be used) can be governed, this means that a leaked token with a long lifespan may pose a significant risk.A more secure alternative is to access Azure DevOps resources using a Microsoft Entra ID (formerly Azure Active Directory) access token.
From the Microsoft Docs:
As PATs are simply bearer tokens, meaning token strings that represent a user’s username and password, they’re incredibly risky to use as they can easily fall into the wrong person’s hands. Microsoft Entra tokens expire every hour […], which limits the overall risk factor when leaked.[1]When considering access to the Azure DevOps Git repositories linked to your Databricks Git folders, you no longer need to rely on PATs. Now, you can use Microsoft Entra ID access tokens, which have tighter controls around token rotation and expiry.
In this blog, we will learn how to use an Entra ID access token as a Git credential in Databricks Git folders to strengthen the security posture when pulling repositories hosted in Azure DevOps.
Prerequisites | Create Service Principal
To start,you need a managed identity or service principal. If you do not have one, follow this document:Register a Microsoft Entra app and create a service principal. At the end of it, you will have a service principal you can use.Note that in this scenario no redirect URI is required, so you can leave that form element blank. Make sure to create a secret and note it down, together with the service principal ID. (The following steps show how you use a service principal as the mechanism for authentication, but the same steps also apply to a managed identity.)
This process assumes that you have an Azure DevOps project set up with a Git repository you would like to link to a Databricks Git folder.
Step 1 | Grant your service principal Reader permissions in your project

UnderAzure DevOps Project settings > Permissions > Readers add your service principal.
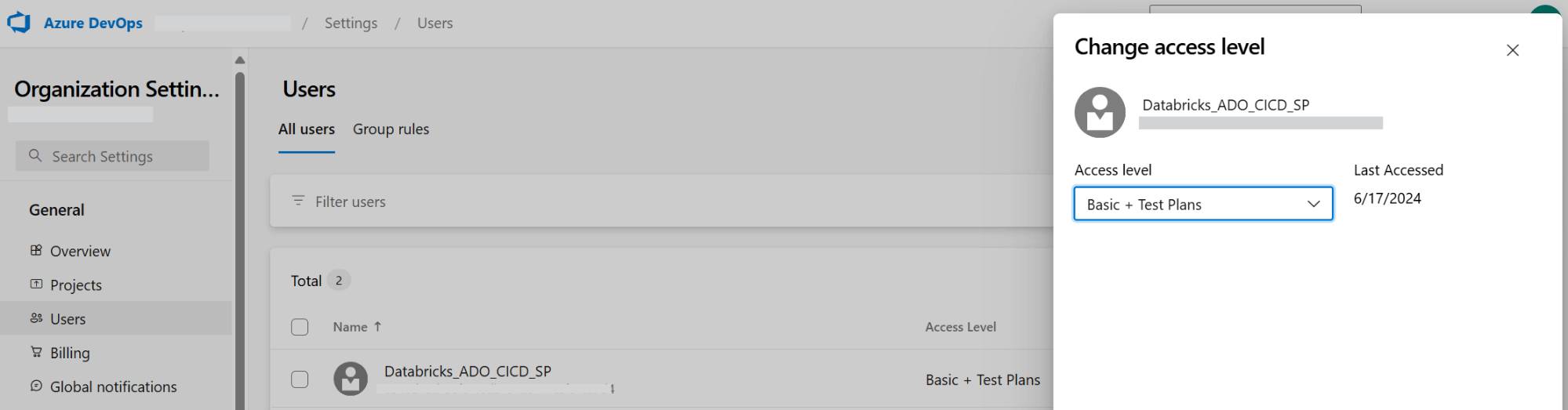
Ensure the access level is sufficient for the required operation under Organization settings > Users.
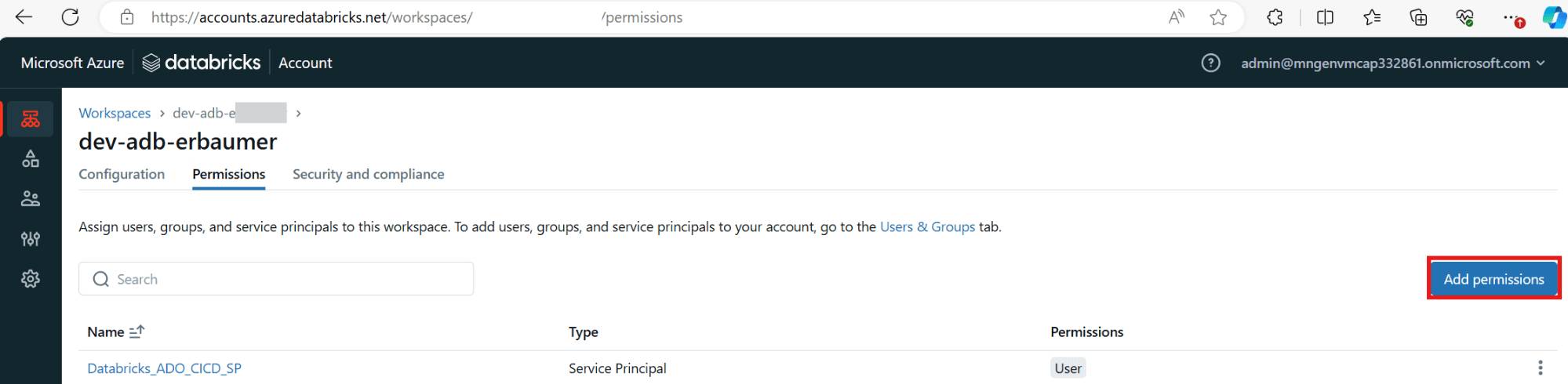
Step 2 | Grant service principal required permissions in Databricks

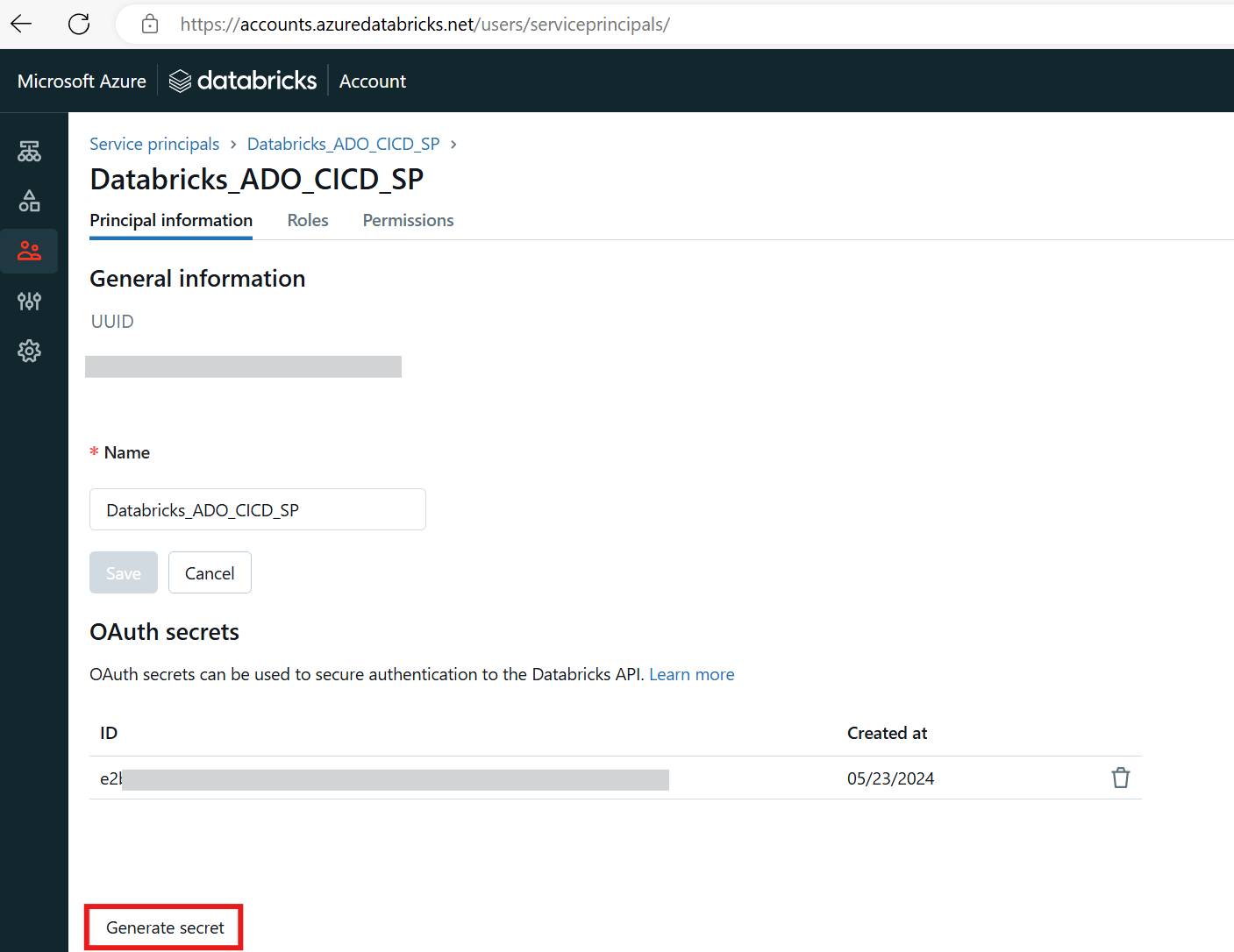
If you use Unity Catalog, open another browser tab and go to your Databricks account console, and then add the service principal to your account.
Now, generate an OAuth secret to authenticate against the Databricks API (using the CLI) and copy it down somewhere secure.
Finally, grant the service principal user permissions on your workspace.
Step 3 | Use the CLI to create Entra ID Token and store it in Databricks Git credential
You’ll use the Azure and Databricks CLI for this step. To authenticate against Databricks, you need a configuration profile (.databrickscfg) configured with the OAuth token we just created, your workspace URL, and a service principal ID. Your update to .databrickscfg should look something like this:
[DEFAULT]host = https://<workspace-url>.azuredatabricks.net/client_id = <service principal ID>client_secret = <Databricks OAuth token value>To log the service principal with the AzureCLI we use the secret we have created earlier. The script requests an Entra ID access token scoped to Azure DevOps (indicated by the UUID 499b84ac-1321-427f-aa17-267ca6975798), then configures a Git credential with the Databricks CLI and uses it to set up our new Git folder:
#!/bin/bash# Prompt user for required inputs and assign to variablesread -p "Enter Service Principal ID: " service_principal_id read -p "Enter Tenant ID: " tenant_id read -p "Enter Service Principal Secret: " service_principal_secretread -p "Enter Service Principal Name: " service_principal_name read -p "Enter your Azure DevOps Organization name: " devops_organization read -p "Enter your Azure DevOps project name: " devops_project read -p "Enter your Azure DevOps repository name: " devops_repo #Login to Azure as the service principalaz login --allow-no-subscriptions --service-principal -u $service_principal_id -p $service_principal_secret --tenant $tenant_id#As the service principal, request an EntraID access token scoped to Azure DevOps. ENTRA_ID_TOKEN=$(az account get-access-token --resource "499b84ac-1321-427f-aa17-267ca6975798" --query "accessToken" --output tsv)#Use the access token instead of a PAT to create a Git credential in Databricks with the service principal's name as git username.#This assumes you have already setup the Databricks CLI .databrickscfg file with workspace, client_id, and client_secretdatabricks git-credentials create azureDevOpsServices --personal-access-token $ENTRA_ID_TOKEN --git-username $service_principal_name#Create a new Databricks repository using the service principal name as the user namedatabricks repos create https://$service_principal_name@dev.azure.com/$devops_organization/$devops_project/_git/$devops_repoSummary | What’s next?
You’ve now learned how to generate Microsoft Entra ID access tokens scoped to Azure DevOps and then store them as a Databricks Git credential instead of as a DevOps PAT token. As the MS Entra ID access token is short-lived, your pipeline must update the Git credential using Databricks git-credentials update, and can then trigger a pull by calling Databricks repos update.As this process just showcases the credential setup, additional security measures are usually required in a production setting, like storing the service principal client secret and the Databricks OAuth token in a secure secret store like Azure Key Vault.
See Use Azure Key Vault secrets in Azure Pipelines and Secret scopes for further details.
