包阅导读总结
1.
关键词:Zero-Trust Security、Docker Containers、Security Model、Docker Desktop、Development Environments
2.
总结:本文介绍了将零信任安全原则应用于基于 Docker Desktop 的开发环境的策略,包括微分段、最小权限访问等,以应对安全风险,强调零信任模型的核心思想及 Docker Desktop 的相关支持特性。
3.
主要内容:
– 零信任安全模型近年受重视,可用于传统系统及容器架构,其核心是不自动信任内外参与者,基于身份和角色授予特权。
– 微分段旨在创建多个保护区域,如测试、培训和生产区,Docker Desktop 可通过特定网络策略实现。
– 遵循最小权限访问原则,增强容器隔离(ECI)能确保参与者仅获最低必要权限,需采用多种措施。
– 基于角色的访问控制(RBAC)用于认证和授权,Docker Desktop 多种方式支持,包括单点登录等。
– 利用 Docker Scout 进行日志记录和支持软件物料清单(SBOM),加强安全,还可通过容器不变性确保容器不被篡改。
思维导图: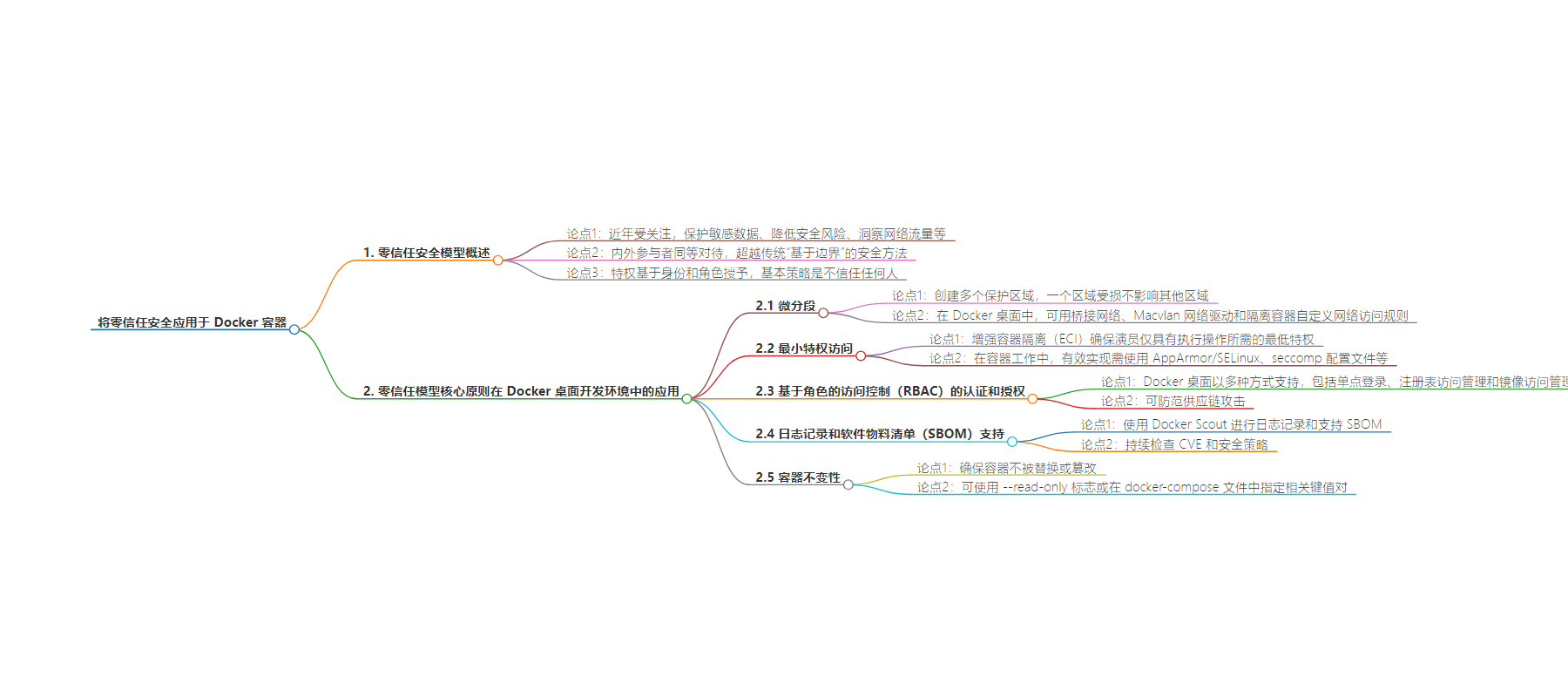
文章来源:infoq.com
作者:Sergio De Simone
发布时间:2024/8/24 0:00
语言:英文
总字数:540字
预计阅读时间:3分钟
评分:86分
标签:零信任安全模型,Docker 容器,微隔离,最小权限访问,容器隔离
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Several strategies exist to apply the principles of zero-trust security to development environments based on Docker Desktop to protect against the risks of security breaches, Docker senior technical leader Jay Schmidt explains.
The zero-trust security model has gained traction in the last few years as an effective strategy to protect sensitive data, lower the risk of security breaches, get visibility into network traffic, and more. It can be applied to traditional systems as well as to container-based architectures, which are affected by image vulnerabilities, cyberattacks, unauthorized access, and other security risks.
The fundamental idea behind the zero-trust model is that both external and internal actors should be treated in the same way. This means going beyond the traditional “perimeter-based” approach to security, where users or machines within the internal perimeter of a company can be automatically trusted. In the zero-trust model, privileges are granted exclusively based on identities and roles, with the basic policy being not trusting anyone.
In his article, Schmidt analyzes how the core principles of the zero-trust model, including microsegmentation, least-privilege access, device access controls, and continuous verification can be applied to a Docker Desktop-based development enviroment.
Microsegmentation aims to create multiple protected zones, such as testing, training, and production, so if one is compromised, the rest of the network can continue working unaffected.
With Docker Desktop, says Schmidt, you can define fine-grained network policies using the bridge network for creating isolated networks or using the Macvlan network driver that allows containers to be treated as distinct physical devices. Another feature that allows to customize network access rule are air-gapped containers.
In keeping with the principle of least-privilege access, enhanced container isolation (ECI) makes it easier to ensure an actor has only the minimum privileges required to perform an action.
In terms of working with containers, effectively implementing least-privilege access requires using AppArmor/SELinux, using seccomp (secure computing mode) profiles, ensuring containers do not run as root, ensuring containers do not request or receive heightened privileges, and so on.
ECI enforces a number of desirable properties, such as running all containers unprivileged, remapping the user namespace, restricting file system access, blocking sensitive system calls, and isolating containers from the Docker Engine’s API.
Authentication and authorization using role-based access control (RBAC) is another key practice that Docker Desktop supports in various ways. These include Single Sign On to manage groups and enforce role and team membership at the account level, and Registry Access Management (RAM) and Image Access Management (IAM) to protect against supply chain attacks.
Another component of Docker Desktop security model is logging and support for software bills of materials (SBOM) using Docker Scout. Using SBOMs enables continually checking against CVEs and security policies. For example, you could enforce all high-profile CVEs to be mitigated, root images to be validated, and so on.
Finally, Docker security can be strengthened through container immutability, which ensures containers are not replaced or tampered with. To this aim, Docker provides the possibility to run a container using the --read-only flag or specifying the read_only: true key value pair in the docker-compose file.
This is just an overview of tools and features provided by Docker Desktop to enforce the zero-trust model. Do not miss the original article to get the full details.
