包阅导读总结
1. 关键词:PEAKLIGHT、Malware、Windows、PowerShell、Downloader
2. 总结:这是一条关于 PEAKLIGHT 恶意软件的检测规则,由 Mandiant 编写,适用于 Windows 平台,用于检测相关事件,规则中包含特定的字符串模式和条件。
3. 主要内容:
– 规则信息:
– 规则名称:M_Downloader_PEAKLIGHT_1
– Mandiant 规则 ID:e0abae27-0816-446f-9475-1987ccbb1bc0
– 作者:Mandiant
– 类别:Malware
– 家族:Peaklight
– 平台:Windows
– 规则描述:
– 旨在检测与 PEAKLIGHT 相关的事件。
– 该恶意软件是混淆的基于 PowerShell 的下载器,检查硬编码文件名并从远程 CDN 下载文件(若文件不存在)。
– 字符串模式:
– 包括多种特定的 ASCII 字符串模式,如与函数、文件操作等相关的模式。
– 检测条件:
– 满足 4 个特定字符串模式,且文件大小小于 10KB。
思维导图: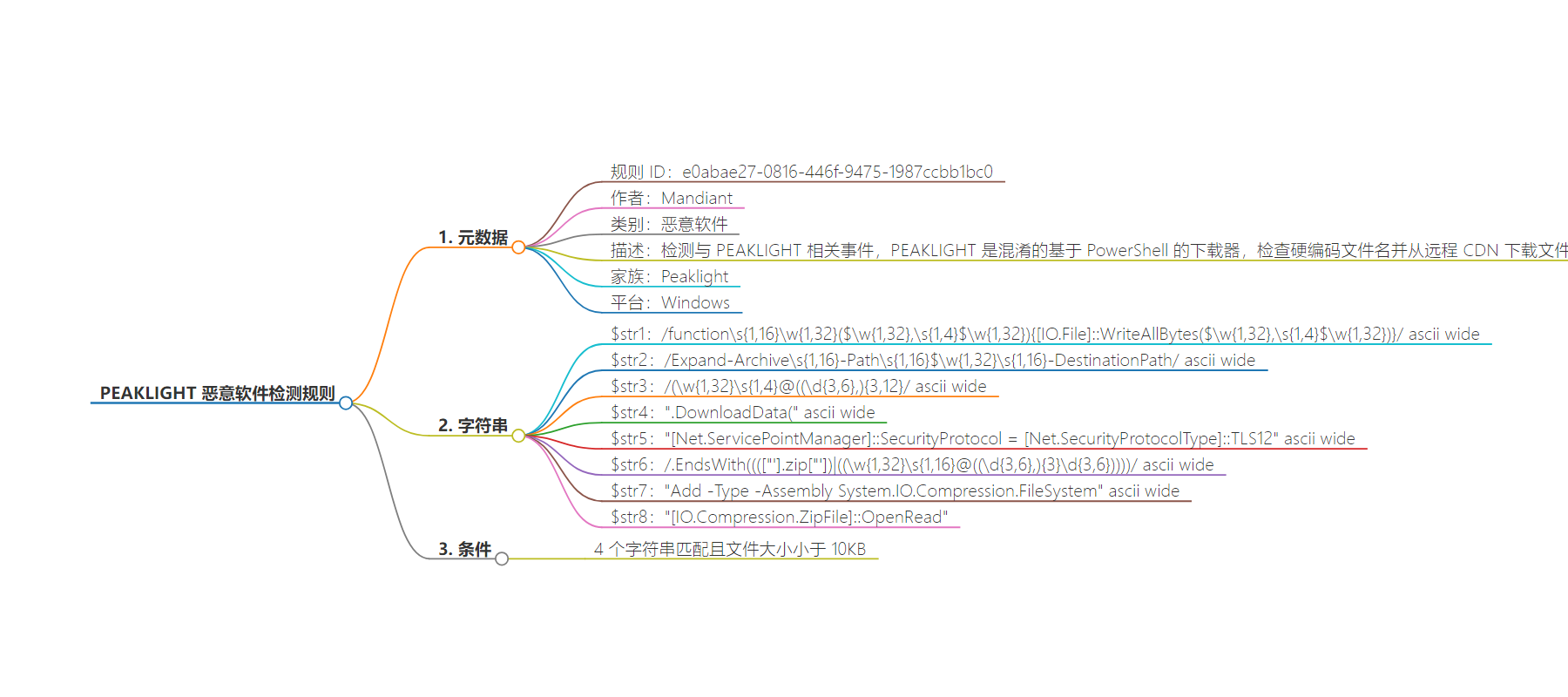
文章来源:cloud.google.com
作者:Mandiant
发布时间:2024/8/22 0:00
语言:英文
总字数:2808字
预计阅读时间:12分钟
评分:84分
标签:恶意软件,内存型投放器,PowerShell,JavaScript 投放器,感染链
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
rule M_Downloader_PEAKLIGHT_1 { meta: mandiant_rule_id = "e0abae27-0816-446f-9475-1987ccbb1bc0" author = "Mandiant" category = "Malware" description = "This rule is designed to detect on events related to peaklight. PEAKLIGHT is an obfuscated PowerShell-based downloader which checks for the presence of hard-coded filenames and downloads files from a remote CDN if the files are not present." family = "Peaklight" platform = "Windows" strings: $str1 = /function\s{1,16}\w{1,32}\(\$\w{1,32},\s{1,4}\$\w{1,32}\)\{\[IO\.File\]::WriteAllBytes\(\$\w{1,32},\s{1,4}\$\w{1,32}\)\}/ ascii wide $str2 = /Expand-Archive\s{1,16}-Path\s{1,16}\$\w{1,32}\s{1,16}-DestinationPath/ ascii wide $str3 = /\(\w{1,32}\s{1,4}@\((\d{3,6},){3,12}/ ascii wide $str4 = ".DownloadData(" ascii wide $str5 = "[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::TLS12" ascii wide $str6 = /\.EndsWith\(((["']\.zip["'])|(\(\w{1,32}\s{1,16}@\((\d{3,6},){3}\d{3,6}\)\)))/ ascii wide $str7 = "Add -Type -Assembly System.IO.Compression.FileSystem" ascii wide $str8 = "[IO.Compression.ZipFile]::OpenRead" condition: 4 of them and filesize < 10KB }