包阅导读总结
1. 关键词:Grafana、安全漏洞、CVE-2024-6837、安全补丁、版本升级
2. 总结:Grafana 发布安全补丁,修复了 CVE-2024-6837 中等严重程度的安全漏洞,该漏洞可通过嵌入的 Swagger API 文档利用,可能导致会话 cookie 被盗等,建议用户尽快升级到已修复的版本。
3. 主要内容:
– Grafana 发布新版本及补丁:
– 发布 Grafana 11.1.4、11.0.3 和 10.4.7 以修复 CVE-2024-6837 漏洞。
– 漏洞详情:
– 利用 /swagger 端点的查询字符串参数注入 HTML 内容,可能引发 XSS 攻击。
– CVSS 评分为 5.4 中等。
– 影响:
– 攻击者可能窃取会话 cookie 或代表登录用户与 API 交互。
– 受影响版本:
– Grafana 10.4.0 至 10.4.6、11.0.0 至 11.0.2、11.1.0 至 11.1.3。
– 解决方案和缓解措施:
– 强烈建议升级到修复版本。
– 实施内容安全策略。
– 时间线和事后审查:
– 从引入问题到发布修复的时间线。
– 报告安全问题:
– 提供报告页面和流程。
– 安全公告:
– 在博客安全类别发布相关信息。
思维导图: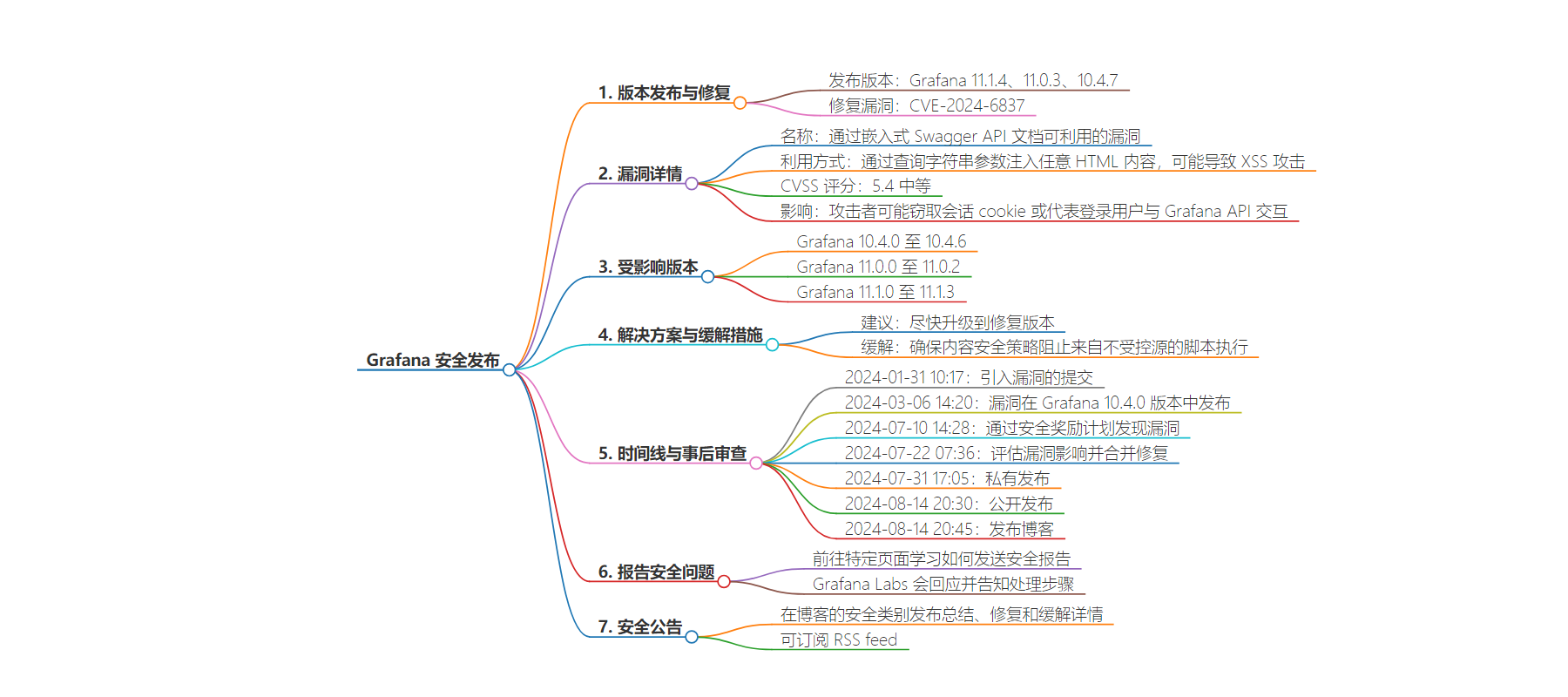
文章来源:grafana.com
作者:Bruno Abrantes
发布时间:2024/8/14 16:45
语言:英文
总字数:527字
预计阅读时间:3分钟
评分:82分
标签:Grafana,安全补丁,CVE-2024-6837,XSS 漏洞,API 安全
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
We’ve recently released Grafana 11.1.4 along with Grafana 11.0.3 and 10.4.7. The latest version of Grafana and these patch releases contain a fix for CVE-2024-6837, a medium severity security vulnerability exploitable through Grafana’s embedded Swagger API documentation.
Release 11.1.4, latest release with the security patch:
Release 11.0.3 with the security patch:
Release 10.4.7 with the security patch:
Appropriate patches have been applied to Grafana Cloud and as always, we closely coordinated with all cloud providers licensed to offer Grafana Cloud Pro. They have received early notification under embargo and confirmed that their offerings are secure at the time of this announcement. This is applicable to Amazon Managed Grafana and Azure Managed Grafana.
Data source permission escalation (CVE-2024-6837)
Summary
Grafana ships with a /swagger endpoint that allows visitors to explore the Grafana API. Through a querystring parameter, it is possible to inject arbitrary HTML content into the page, which in turn allows for the possibility of an XSS exploit.
The CVSS score for this vulnerability is 5.4 Medium.
Impact
An attacker who can successfully exploit this vulnerability may be able to steal session cookies or interact with the Grafana API on behalf of the logged in user who is visiting the page.
Impacted versions
The vulnerability impacts Grafana OSS and Grafana Enterprise running on the following versions:
- Grafana 10.4.0 to Grafana 10.4.6
- Grafana 11.0.0 to Grafana 11.0.2
- Grafana 11.1.0 to Grafana 11.1.3
Appropriate patches have been applied to Grafana Cloud.
Solutions and mitigations
If your instance is vulnerable, we strongly recommend upgrading to one of the patched versions as soon as possible.
As a mitigation, make sure that a Content Security Policy that blocks script execution coming from sources outside of the domains you control. For example:
Content-Security-Policy: script-src 'self';Timeline and post-incident review
Here is a detailed incident timeline starting from when we originally introduced the issue. All times are in UTC.
- 2024-01-31 10:17 A commit enabled the
queryConfigEnabledSwagger flag, introducing the vulnerability. - 2024-03-06 14:20 – The vulnerability is released in Grafana version 10.4.0.
- 2024-07-10 14:28 – The vulnerability is discovered through our Security Bounty program
- 2024-07-22 07:36 – The impact of the vulnerability is assessed, and a fix is merged.
- 2024-07-31 17:05 Private release.
- 2024-08-14 20:30 – Public release.
- 2024-08-14 20:45 Blog published.
Reporting security issues
If you think you have found a security vulnerability, please go to our Report a security issue page to learn how to send a security report.
Grafana Labs will send you a response indicating the next steps in handling your report. After the initial reply to your report, the security team will keep you informed of the progress towards a fix and full announcement, and may ask for additional information or guidance.
Important: We ask you to not disclose the vulnerability before it has been fixed and announced, unless you received a response from the Grafana Labs security team that you can do so.
Security announcements
We maintain a security category on our blog where we will always post a summary, remediation, and mitigation details for any patch containing security fixes. You can also subscribe to our RSS feed.
