包阅导读总结
1. 关键词:Passkeys、Auth0、Authentication、Passwordless、Login
2. 总结:本文介绍了 Auth0 中的 Passkeys,包括其在各计划中的可用性、与密码的关系、设备和浏览器兼容性、配置要点、安全保护及管理等常见问题及相关信息。
3. 主要内容:
– Passkeys 概述
– 众多资源和各厂商的不同实现
– 常见问题解答
– 免费层级可用
– 作为额外认证选项,未完全取代密码
– 用户可仅用 Passkeys 登录或注册,也可继续使用密码
– 现有密码用户可添加 Passkeys
– 设备和浏览器兼容性
– 参考相关资源获取最新支持信息
– 在 Auth0 中启用
– 位置和操作
– 相关前提条件
– 登录选项
– 配置
– 本地注册
– 渐进式注册
– 安全与攻击保护
– 防范 QR 码滥用
– 蓝牙要求及影响
– 攻击保护措施适用
– MFA 政策适用
– 管理和处理
– 租户日志中的调试方法
思维导图: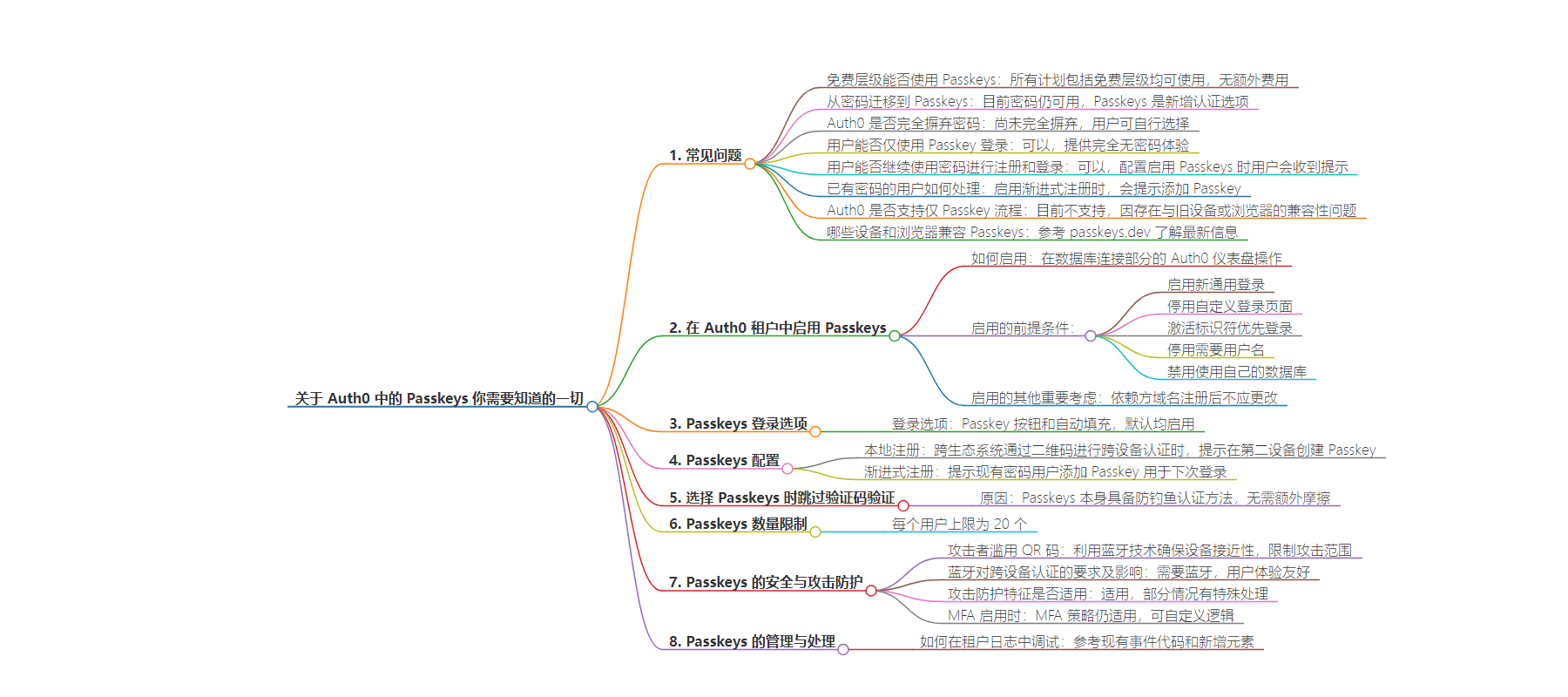
文章地址:https://auth0.com/blog/all-you-need-to-know-about-passkeys-at-auth0/
文章来源:auth0.com
作者:Auth0 Blog
发布时间:2024/9/11 15:47
语言:英文
总字数:1815字
预计阅读时间:8分钟
评分:80分
标签:密码钥匙,Auth0,无密码认证,WebAuthn,安全性
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
There are so many resources for passkeys, and each vendor has its implementation of the standard.
If you still need to familiarize yourself with passkeys, I recommend you look at this blog post.
Now, let’s answer some of your frequently asked questions about passkeys at Auth0!
Can I Use Passkeys With The Free Tier?
Starting with the elephant in the room, let’s leave this clear here and now: Passkeys are included in ALL PLANS, yes, including the Free Tier, at no additional cost. We really, really* are aiming for a passwordless future, and this is part of our commitment to it.
Migrating from Passwords to Passkeys
The industry is moving towards a passwordless future, and at Auth0, we are committed to the same goal.
Is Auth0 getting Rid of Passwords Entirely?
Not yet. For now, we introduced passkeys as an additional authentication option alongside passwords. Users can choose between a passkey and a password based on what works best.
Can your Users Only Use a Passkey for Login?
Yes, absolutely. End users can sign up and log in using only passkeys, providing a completely passwordless experience. Passkeys serve as a robust first and primary factor for account authentication, designed to enhance security and offer a more user-friendly experience. The goal is eventually to replace passwords.
Can your Users Continue to Use Passwords for Signup & Login?
Yes. If passkeys are enabled in the configuration, end users will be prompted to continue with a passkey or a password.
What About the Existing Users with Passwords?
When you enable progressive enrollment in the Auth0 Dashboard, existing users with passwords will be prompted to add a passkey so that they can use it in subsequent logins.
Does Auth0 Support a Passkey-Only Flow (a flow where there is no password involved anywhere)?
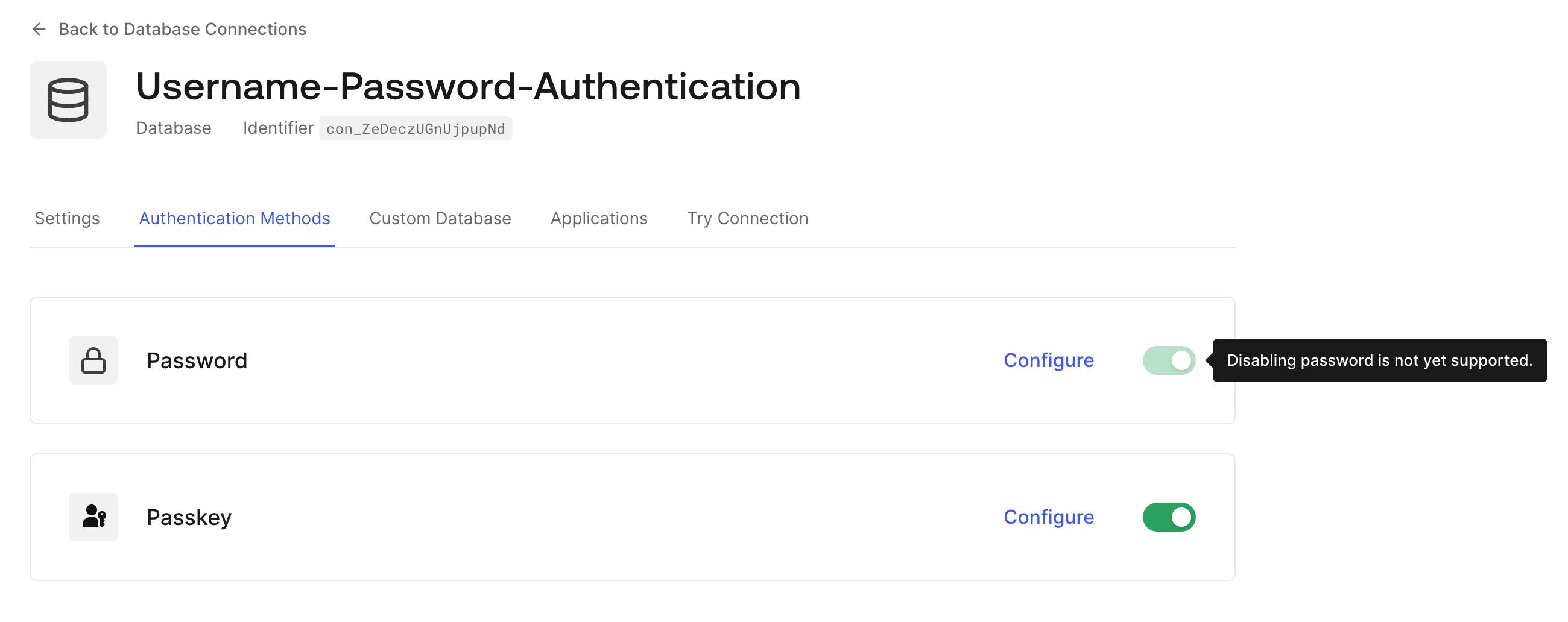
Not at the moment. We are keeping the option of using passwords alongside passkeys; there are still some challenges regarding compatibility issues with older devices or browsers that need passkey support. In such cases, passwords will remain a viable method of authentication.
In other words, disabling password is not yet supported in the Database connection.
Which Device and Browser are Compatible with Passkeys?
Passkeys are compatible with different operational systems and browsers at differing levels. Please refer to passkeys.dev Device Support (maintained by W3C WebAuthn Community Adoption Group and members of the FIDO Alliance) which provides latest information on device/browser support on passkeys.
You can learn more about passkeys and see them in action in this excellent session from Oktane 2023.
Enabling Passkeys in Your Auth0 Tenant
You can enable passkeys by switching a toggle, and you can always refer to the documentation to understand how the signup and login flow with passkeys work at Auth0, but let’s answer some more specific questions about enabling passkeys:
How Can You Enable Passkeys for Your Users?
Passkeys are available in the Database connection section in the Auth0 Dashboard. You could enable passkeys by logging in to your Auth0 Dashboard and navigating to Authentication -> Database -> Connection -> Authentication Methods -> Passkey as shown in the below screenshot.
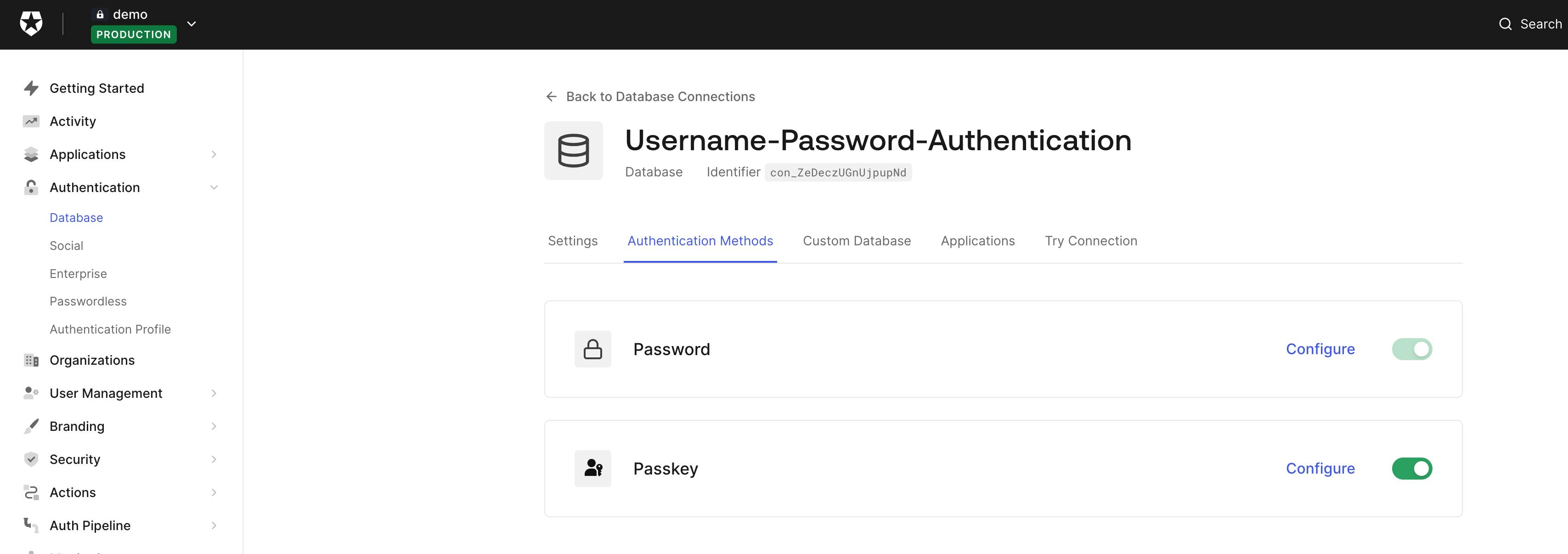
For more details on enabling passkeys, follow the steps in this blog post.
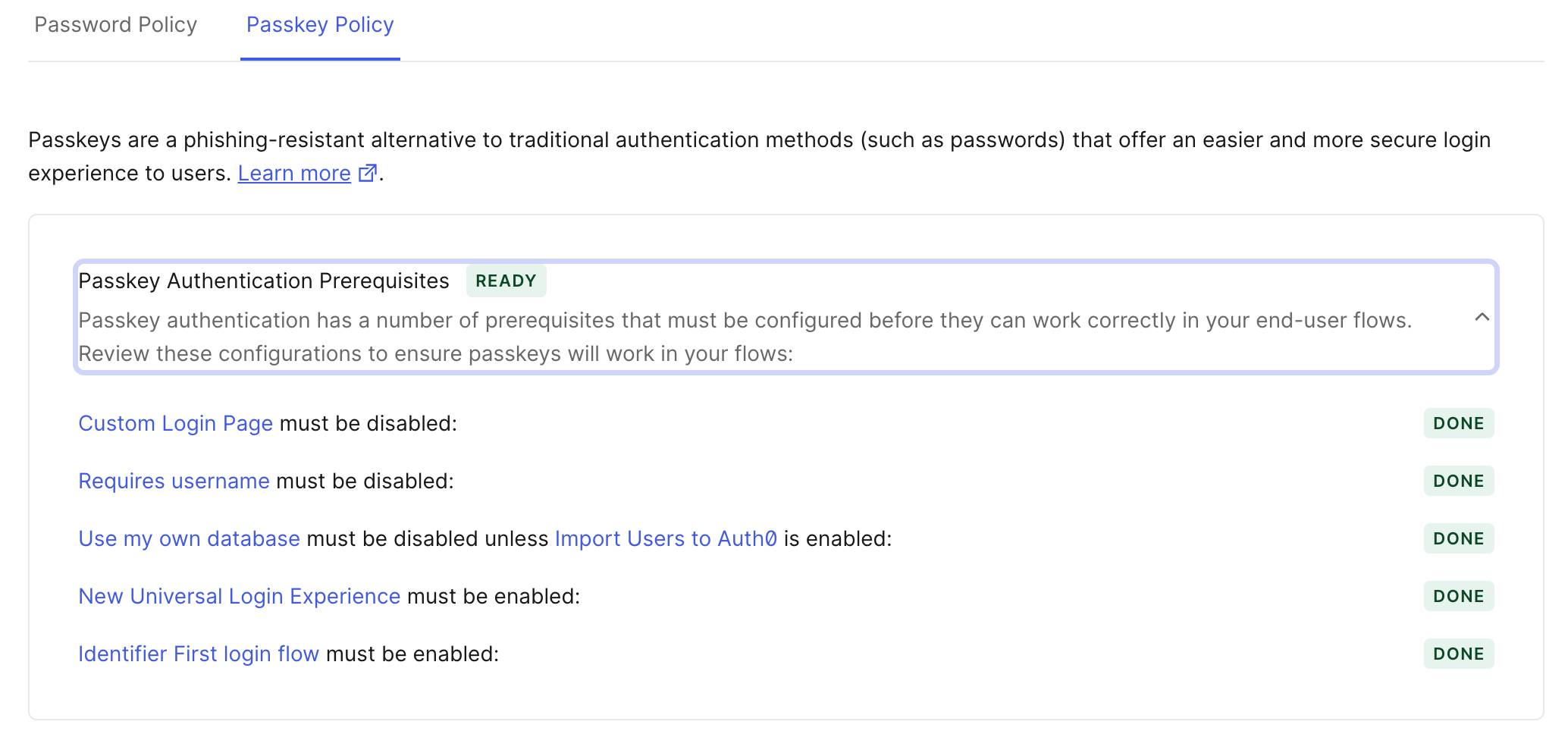
Are there any prerequisites to enable passkeys?
Yes, passkeys come with specific prerequisites:
-
Enable New Universal Login: we encourage you to switch to New Universal Login, where new features like passkeys are being introduced.
-
Deactivate Custom Login Page: Enabling the Custom Login Page reverts the New Universal Login to the Classic experience, which connects to the first requirement.
-
Activate Identifier First Login: This facilitates a seamless user journey, beginning with the Identifier. Users can then decide whether to proceed with passkey or password authentication.
-
Deactivate Requires username: For connections that have not activated attributes for flexible identifiers, the username is not supported. To use passkeys with usernames, you will need to activate attributes for flexible identifiers on the connection.
-
Disable Use my own database: Finally, “Use my own database” must be disabled unless Import Users to Auth0 is enabled as it implies passkeys created in the system will remain separate from user credentials stored in external custom databases (unless Lazy migration is ON).
If you are missing any of the prerequisites above, we will show a checklist similar to the image below when you try to enable passkeys for your users.
Is there any other important consideration for enabling passkeys?
An important point to note is the relying party domain should not change after passkeys are enrolled, because changing the domain will invalidate all existing passkeys. As such, passkeys are created for a specific RP domain.
Are there different options for logging in with passkeys?
Yes. You could choose how the passkey options are rendered in their end user prompts. This will control how the challenge is triggered.
Two options are available for logging in with passkeys: Passkey Button and Autofill. By default, both options are enabled when passkeys are configured.
As per FIDO UX guidelines, FIDO research explored participants’ success and satisfaction with dedicated passkey buttons and autofill. FIDO testing indicates that autofill ensured the highest success for people to sign in with a passkey.
However, it is essential to note that autofill does not work in all scenarios. For example, when autofill is disabled in the browser, the Passkey Button provides the fallback UX.
Passkeys Configuration at Auth0
What is Local Enrollment?
When you enable local enrollment and authenticate through the cross-device flow (using a QR code) across ecosystems, Auth0 will prompt the user to create a passkey on their second device. Local enrollment ensures secure and effortless logins, as the passkeys from the second device become accessible for subsequent logins. It also eliminates the need for the user to repeatedly use a QR code to log on to the second device; instead, they can simply utilize the local passkey for all subsequent logins.
What is Progressive Enrollment?
Progressive enrollment allows Auth0 to prompt existing users with passwords to add passkeys so they can use them for their next login.
Why is Auth0 Skipping Captcha Verification When Passkeys are Selected?
Passkeys already offer a phishing-resistant authentication method. To achieve a faster, seamless, and secure login experience, adding additional friction during login steps like Captcha is not optimal. Hence, Captcha verification is presented, but users can skip this step when they select log in with a passkey. They still have to solve a Captcha if they’re presented with one and choose to continue with the password.
Does Auth0 have any limit on the number of passkeys per user?
Yes. For now, we’ve implemented a limit of 20 passkeys per user. A user could have multiple passkeys. For example, a user could create a passkey on Apple and Google devices when they authenticate via cross-device authentication using a QR code.
Security & Attack Protection with Passkeys
What if An Attacker Tries to Abuse a QR Code?
FIDO cross-device authentication incorporates an inherent verification mechanism utilizing Bluetooth technology to ensure the proximity of the two devices. While this process remains seamless for the user, potential attackers who acquire a QR code and attempt remote logins will be thwarted, as the cross-device authentication does not operate over remote connections. We’re limiting the attack surface to a few meters of physical proximity instead of anywhere in the world, as with passwords.
Is Bluetooth a Requirement for Cross-Device Authentication? How does it Impact the Overall User Experience?
Yes. The Bluetooth-based proximity verification for cross-device authentication happens seamlessly for the end user. If they have deactivated Bluetooth, a user-friendly prompt will guide them to enable Bluetooth when they scan a QR code for cross-device authentication.
Are Attack Protection Features Applicable to Passkeys?
Yes. Certain attack protection features, such as Suspicious IP throttling, will be applicable for passkeys. Credential Guard is skipped when utilizing a passkey due to the absence of a password. While Bot Detection will operate during the pre-login assessment phase, the Captcha verification step is bypassed when opting for passkey-based logins.
What if MFA is Enabled in the Flow?
The MFA policy will continue to apply for login with passkeys. This implies that users will be prompted with a second factor depending on their MFA configuration. If you choose to bypass a second factor, you could implement custom logic when a passkey is used as an authentication method.
Can I use Passkeys as a Second Factor?
Not for now. Passkeys are the first and primary factor for account authentication, designed to enhance security and offer a more user-friendly experience. The goal is to eventually replace passwords.
Managing and Handling Passkeys
How can you debug passkeys in your tenant logs?
Passkeys are an additional authentication method. Therefore, we’re repurposing existing event codes outlined in Log Event Type Codes. However, to enhance clarity regarding the employed authentication method, we’ve incorporated the following elements:
-
Signup: The event with type
sswill include a fielddetails.authentication_methodset to eitherpasswordorpasskeybased on the method used during signup. -
Login: For passkey-based logins,
"performed_amr": ["phr"]is included. During login, the event with typesindicates if a passkey is used to authenticate. Thedetails.promptsarray contains the set of prompts that the end-user navigated through, and the"performed_amr": ["phr"]will be present on the element if passkey authentication was used (phrstands for “phishing-resistant” and is the standard amr (Authentication Method Reference) claim value for passkeys). -
Progressive & local enrollment: Successful enrollment will be captured with
gd_enrollment_complete, while failed enrollment attempts will be recorded asgd_webauthn_enrollment_failed.
Can you Use Passkeys with the Management API?
Yes, you can list and revoke passkeys using the Auth0 Management API. You can learn more about managing passkeys with this blog post.
Can you Use Passkeys with Actions?
Yes. You can, for example, detect whether a user authenticates with a passkey within the Post-Login trigger.
In the event object, the authentication.methods array contains elements describing the methods used to authenticate for the current session. The elements’ names are set to pwd for regular password-based authentication and passkey for passkey-based authentication.
Account Recovery
How can users recover their passkeys?
Auth0 stores a record of public information about your passkey (such as the public key) that you can use for authentication. As passkeys are stored within their respective ecosystems (like Apple or Google) and not shared with the relying party (such as Auth0), end users must retrieve passkeys directly from these ecosystems when needed.
How could users recover an account?
The existing account recovery process remains unchanged. Users will still need to verify their email by clicking the link in their inbox. Following successful verification, they’ll have the option to set up a new password.
We hope this passkeys FAQ helps you leave passwords behind and enable passkeys for your users today. If you have other questions, make sure to post them in the comments, and our team will be happy to help!
