包阅导读总结
1. 关键词:Kubernetes、云安全、威胁追踪、攻击指标、日志分析
2. 总结:上个月在 Linux 基金会的会议上,来自 Mitiga 的专家讨论在 Kubernetes 环境中利用日志追踪威胁者。强调不能对云安全自满,需积极搜寻攻击者踪迹,介绍了威胁追踪方法和关键攻击指标,指出要主动探寻威胁。
3. 主要内容:
– 安全专家 Stav Ochakovski 和 Ariel Szarf 在会议上探讨 Kubernetes 环境中的威胁追踪
– 指出攻击者可能已在云化的 Kubernetes 集群中
– 强调不能对云安全掉以轻心,迁移易给攻击者可乘之机
– 将现代威胁追踪比作“找沃尔多”游戏,应积极搜索攻击者踪迹
– 方法包括提出潜在攻击假设,列出攻击指标,调查可疑活动
– 以假设场景说明 Kubernetes 集群可能被攻破的情况
– 列举需关注的三个关键指标
– 强调收集相关日志以发现攻击前兆的重要性
– 总结强调要主动用正确工具、知识和疑问搜寻威胁
思维导图: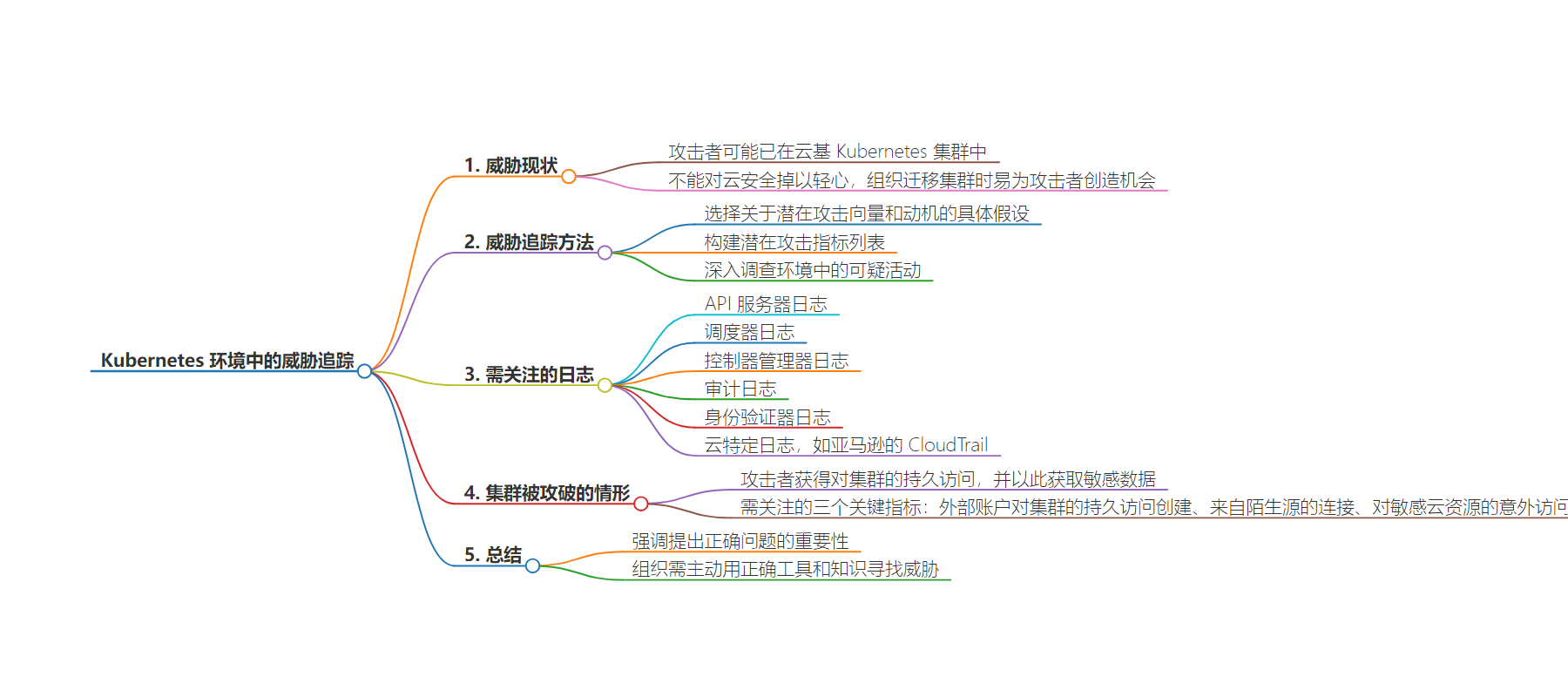
文章地址:https://thenewstack.io/hunting-the-stealth-hacker-in-the-kubernetes-jungle/
文章来源:thenewstack.io
作者:Steven J. Vaughan-Nichols
发布时间:2024/7/10 19:32
语言:英文
总字数:524字
预计阅读时间:3分钟
评分:84分
标签:Kubernetes 安全,云安全,威胁狩猎,日志分析,Mitiga
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
SEATTLE — At the Linux Foundation‘s CloudNativeSecurity Conference last month, security experts Stav Ochakovski and Ariel Szarf from Mitiga, a cloud and software as a service (SaaS) security company, discussed how they use logs to track down threat actors in a Kubernetes environment.
After all, as Ochakovski said, the attackers are likely already in your cloud-based Kubernetes clusters. Indeed, Ochakovsk remarked, “It’s not about whether there is or isn’t a threat actor in a Kubernetes environment. It’s about where it is.”
They argue that you can’t be complacent about cloud security. That’s because as organizations increasingly migrate their Kubernetes clusters to the cloud, lured by the promise of scalability and managed services, they all too often unwittingly open doors to sophisticated attackers.
Ochakovski and Szarf vividly described modern threat hunting as a high-stakes game of “Where’s Waldo?” Thus, they argue, you should aggressively search for attackers’ tracks even when you don’t see signs of them.
After all, “Sometimes, bad actors succeed in compromising an environment without triggering detection services,” Szarf said,
Their methodology is both systematic and intuitive. It begins with choosing a concrete hypothesis about potential attack vectors and motivations. For instance, an attacker might target sensitive data in cloud storage buckets.
The next step involves building a list of potential attack indicators, followed by a thorough investigation of any suspicious activities in the environment. Any anomaly may be a sign that an enemy is near.
How do you spot these? By closely looking at your API server logs, scheduler logs, controller manager logs, audit logs and authenticator logs from Kubernetes, as well as cloud-specific logs such as Amazon Web Services’ CloudTrail.
How Your Kubernetes Cluster Could Be Breached
The presenters walked through a hypothetical scenario where an attacker gains persistent access to a Kubernetes cluster and uses it as a springboard to access sensitive data.
They highlighted three key indicators to watch for: the creation of persistent access to the cluster from an external account, connections to the cluster from unfamiliar sources and unexpected access to sensitive cloud resources.
Ochakovski and Szarf stressed the importance of enabling and collecting relevant logs from the Kubernetes ecosystem and the cloud provider to find these silent precursors of an attack. These logs are the footprints that security teams can follow to uncover potential threats.
“If there is one key takeaway we want you to take from this talk, it’s all about asking the right questions,” Ochakovski concluded. This sentiment encapsulates the essence of effective threat hunting – a proactive, curious mindset that assumes the presence of threats and actively seeks them out.
In short, it’s not enough to hope for the best. Organizations must proactively hunt for threats armed with the right tools, knowledge and, most important of all, the right, suspicious questions.
If that sounds paranoid, well, as the saying goes, “It’s not paranoia if they really are out to get you.” And, when it comes to Kubernetes clusters on public clouds, attackers really are out to get you.
YOUTUBE.COM/THENEWSTACK
Tech moves fast, don’t miss an episode. Subscribe to our YouTubechannel to stream all our podcasts, interviews, demos, and more.
