包阅导读总结
1. 关键词:PQC、量子计算、加密算法、标准、业务影响
2. 总结:本文探讨了为后量子密码(PQC)做准备的必要性,包括量子攻击对业务的影响、密码迁移的耗时、未来数据安全风险、标准和法规的推动等,强调组织应立即着手制定并实施 PQC 策略。
3. 主要内容:
– 谷歌参与量子计算标准制定
– 工程师为标准组织做贡献
– 与伙伴合作生产验证的 PQC 实现
– 准备 PQC 的原因
– 密码失效的业务影响
– 密码迁移耗时长
– 未来可能解密现窃数据
– 标准化和即将到来的法规
– 从准备到行动
– 制定 PQC 策略
– 实施 PQC 策略,获取专业知识
– 评估业务风险
– 分析更广泛风险
– 借鉴过去经验
– 强调立即过渡的重要性
– 量子计算机威胁不确定但任务艰巨
– 面临监管等方面对 PQC 计划的问询
思维导图: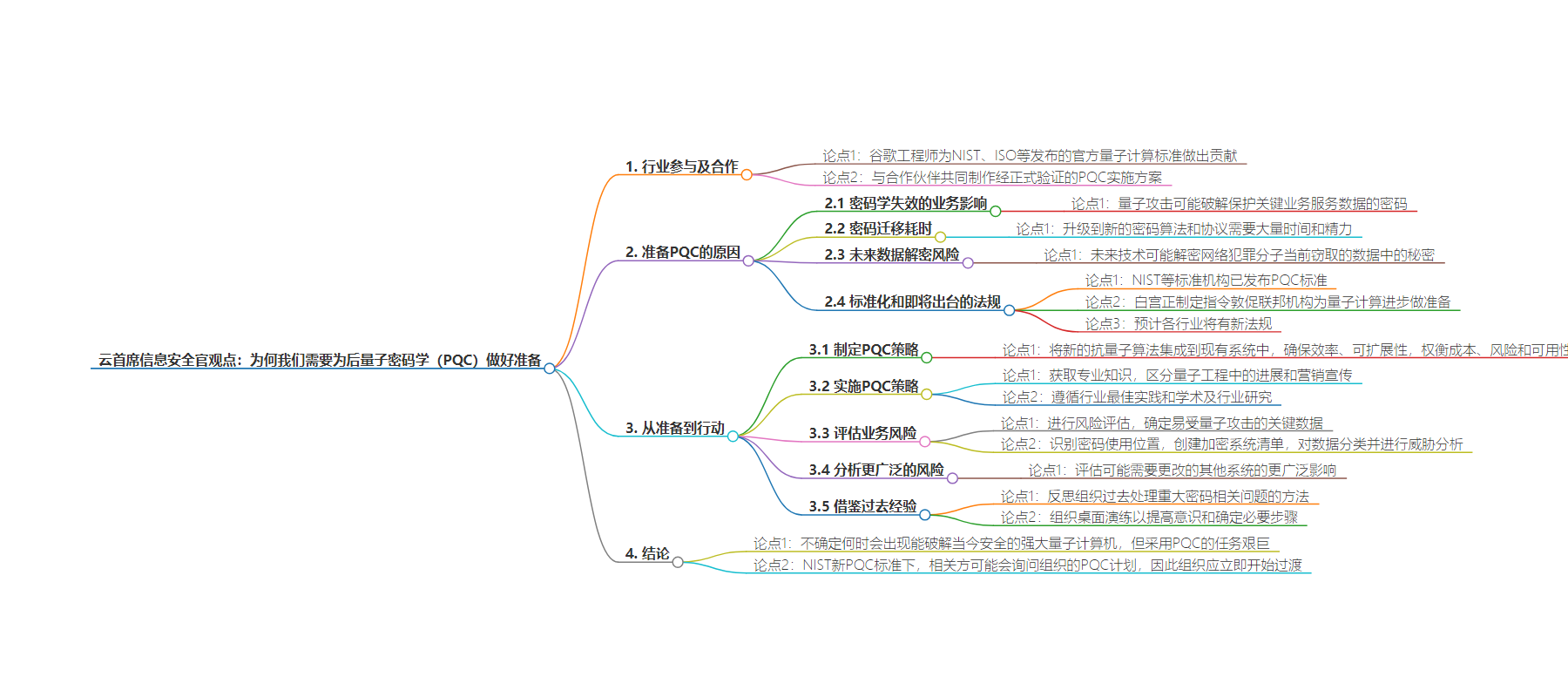
文章来源:cloud.google.com
作者:Phil Venables
发布时间:2024/8/15 0:00
语言:英文
总字数:1915字
预计阅读时间:8分钟
评分:83分
标签:后量子密码学,网络安全,量子计算,Google 云,风险管理
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Additionally, Google engineers have contributed to official, formal quantum computing standards released by NIST, ISO, and other standards organizations, and we are working with partners to produce formally-verified PQC implementations that can be used at Google and beyond.
Board members should understand the consequences of not preparing for PQC, and ask questions of their organization’s leaders including the CISO, CIO, and CTO, and despite the unpredictable timeline for quantum breakthroughs.
There are four primary reasons that drive our interest in getting ready for PQC now — and not delaying action.
- Business impact of cryptography failing. Quantum attacks could be able to break the cryptography used to protect data critical to delivery of your most important business services.
- Migrating cryptography takes a long time. Although quantum-safe cryptographic algorithms are available and can be implemented on existing hardware, upgrading to new cryptographic algorithms and protocols requires significant time and effort.
- Harvest now, decrypt later. Future technology could unlock the secrets hidden in data that cybercriminals are stealing today — secrets that could be the very lifeblood of your organization, such as intellectual property, trade secrets, and sensitive communication records.
- Standardization and upcoming regulations. Well-recognized standards bodies, including NIST, have just released post-quantum cryptography standards. Even the White House is developing directives urging federal agencies to prepare for quantum computing advancements. We anticipate new regulations across various industries, and Google is actively participating in working groups such as the Financial Services Information Sharing and Analysis Center (FS-ISAC) and the PQC Alliance to address these developments.
From PQC preparation to PQC action
Preparing for PQC doesn’t need to be managed as a “big bang”. Board members should speak with their CISO, CIO, and CTO about developing a post-quantum cryptography strategy. This should include preparing for integration of new, quantum-resistant algorithms into existing systems, while ensuring efficiency and scalability and weighing cost, risk, and usability.
- Implement a PQC strategy: Acquire expertise to distinguish between hyped up announcements of small improvements, marketing, and actual advancement in quantum engineering. Follow up with both industry best practices including our post-quantum cryptography blogs and academic and industry research, including Google’s Quantum Research.
- Assess the business risk: Conduct a risk assessment to identify critical data that is most vulnerable to quantum attacks. Identify where cryptography is utilized — it is likely pervasive throughout your systems. Create an inventory of all systems employing cryptography to safeguard data at rest, in transit, and in use. Classify the data and perform a threat analysis. Google’s quantum threat analysis can serve as an example of how to determine which changes should be addressed first.
- Analyze the broader risk: Assess the wider impact to other systems that might need to change. This could be like a Y2K problem where the format of data (for example, larger digital signatures) in databases and applications might need significant software changes beyond the cryptography.
- Learn from the past: Reflect on how your organization successfully dealt with major cryptography-related issues in the past. This will help identify strategies that worked well and areas for improvement. Organize a tabletop exercise — a workshop for the organization’s leadership (and board members) to raise awareness of the complexities associated with migrating cryptographic systems — and to identify the necessary steps moving forward. Google’s adoption of PQC can serve as an example for other organizations.
To be clear, we’re not sure of exactly when we’ll see a quantum computer powerful enough to break today’s security. Whether it happens in 5, 10, or 15 years, the task of adopting post-quantum cryptography is substantial.
Additionally, with NIST’s new PQC standards, regulators, governments, customers, and auditors are likely to question your organization about its PQC plans. Therefore, it’s crucial for organizations to initiate the transition immediately.
For more leadership guidance from Google Cloud experts, please see our CISO Insights hub and contact us at Ask Office of the CISO.
