包阅导读总结
1. 关键词:JSON Web Tokens、认证、授权、安全、结构
2. 总结:本文深入探讨了 JSON Web Tokens(JWTs),包括其结构、创建与验证流程、安全考虑、常见漏洞及应对措施,强调理解这些方面以有效利用 JWTs 提升应用安全和用户体验。
3. 主要内容:
– JSON Web Tokens 简介
– 是现代认证和授权的基石
– 提供安全高效的双方信息传递方式
– JWT 的结构
– 由头、载荷、签名三部分组成
– 头包含元数据
– 载荷携带声明
– 签名确保完整性
– 创建和验证 JWTs
– 创建步骤
– 验证流程
– 可使用相关库
– 安全考虑
– 密钥管理
– 过期时间设置
– 令牌撤销
– 使用 HTTPS
– 避免敏感数据
– 防范劫持
– 常见 JWT 漏洞
– 签名伪造
– 载荷篡改
– 过期时间操纵
– 暴力攻击
– 注入攻击
– 信息泄露
– 总结
– JWTs 是强大机制但非万能
– 需实施健全安全实践
思维导图: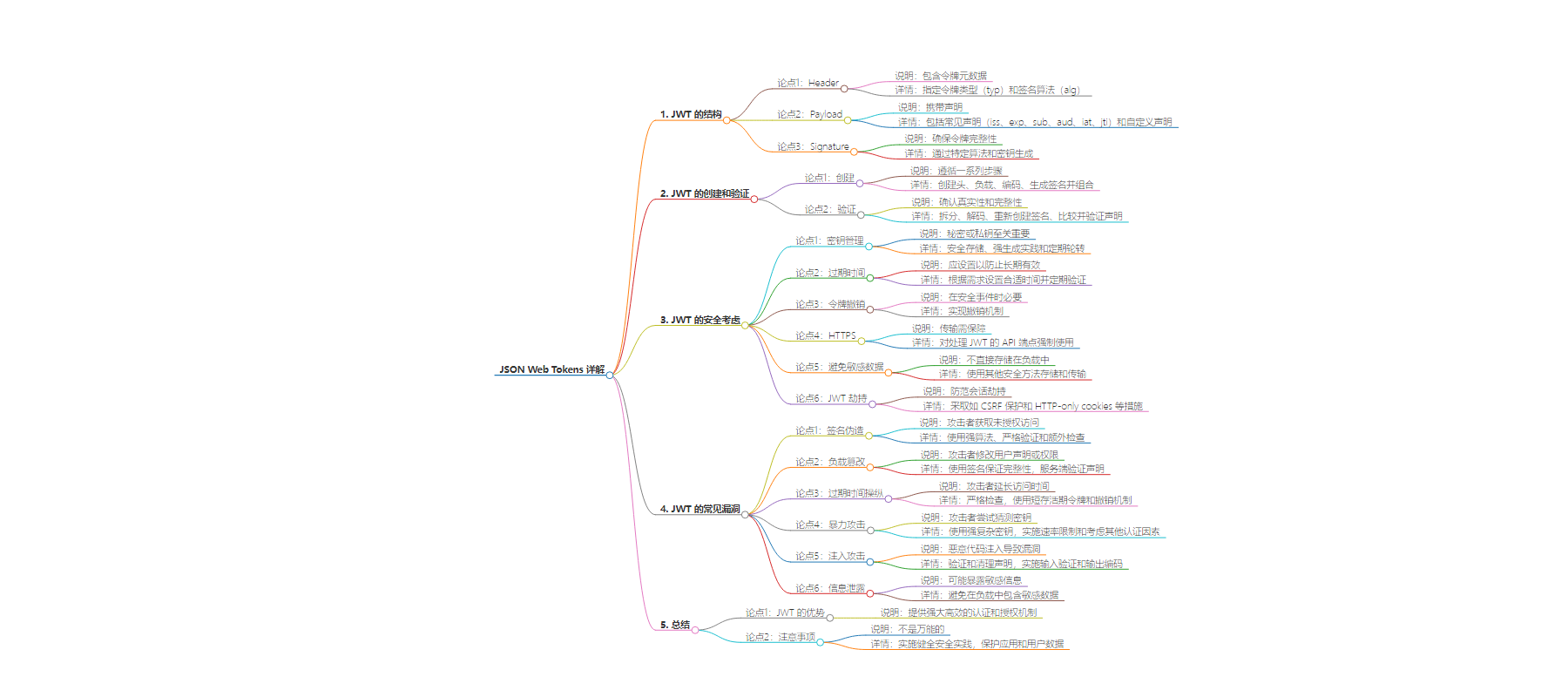
文章地址:https://www.javacodegeeks.com/2024/08/deep-dive-into-json-web-tokens.html
文章来源:javacodegeeks.com
作者:Eleftheria Drosopoulou
发布时间:2024/8/20 12:54
语言:英文
总字数:977字
预计阅读时间:4分钟
评分:86分
标签:JSON Web 令牌,认证,授权,安全,基于令牌的认证
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
JSON Web Tokens (JWTs) have become a cornerstone of modern authentication and authorization. They offer a secure and efficient way to represent claims securely between two parties. This guide will delve into the intricacies of JWTs, exploring their structure, components, creation, verification, and best practices.
By the end of this deep dive, you will have a comprehensive understanding of JWTs and be equipped to implement them effectively in your applications.
1. The Structure of a JWT
A JWT is composed of three distinct parts, separated by dots (.):
1. Header
The header contains metadata about the token itself, including:
- typ: Specifies the token type, which is always “JWT.”
- alg: Indicates the algorithm used to sign the token. Common algorithms include HS256 (HMAC SHA-256), RS256 (RSA with SHA-256), and ES256 (ECDSA using P-256 curve and SHA-256).
Example:
{ "typ": "JWT", "alg": "HS256"}
2. Payload
The payload carries claims, which are statements or pieces of information about the entity being authenticated. These claims can include:
- iss: Issuer of the token
- exp: Expiration time
- sub: Subject of the token
- aud: Audience the token is intended for
- iat: Issued at time
- jti: Unique identifier
Custom claims can also be added to convey specific information.
Example:
{ "sub": "1234567890", "name": "John Doe", "admin": true, "exp": 1516239022}
3. Signature
The signature ensures the integrity of the token. It is generated by signing the header and payload using the secret key or private key specified in the header.
Example:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZCI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyLCJleHAiOjE1MTYyMzgyMjJ9.Y29kZWRvdXRyb25rZXk=
In this example, the first part is the base64-url-encoded header, the second part is the base64-url-encoded payload, and the third part is the signature.
2. Creating and Verifying JWTs
Creation
To create a JWT, follow these steps:
- Create the header: This typically includes the token type (
typ) and the signing algorithm (alg). - Create the payload: Include necessary claims such as the issuer, expiration time, subject, and any custom data.
- Base64URL encode both the header and payload.
- Create a signature: Use the specified algorithm, a secret key (for HMAC-based algorithms) or a private key (for asymmetric algorithms), and the encoded header and payload to generate a signature.
- Combine the encoded header, payload, and signature with dots (
.) to form the final JWT.
Verification
When receiving a JWT, follow these steps to verify its authenticity and integrity:
- Split the token into header, payload, and signature parts.
- Decode the header and payload to obtain their original JSON structures.
- Recreate the signature using the same algorithm and secret/public key as used during creation.
- Compare the recreated signature with the received signature. If they match, the token is valid.
- Validate claims: Check for expiration, issuer, audience, and other relevant claims to ensure the token is still valid and intended for the correct recipient.
While it’s possible to implement JWT creation and verification manually, libraries like
jsonwebtokenin Node.js provide convenient abstractions for these processes.
3. Security Considerations for JWTs
JWTs offer a convenient method for authentication and authorization, but they require careful handling to mitigate security risks. Consider the following key points:
| Security Consideration | Explanation | Mitigation Strategies |
|---|---|---|
| Secret/Private Key Management | The secret or private key used to sign JWTs is crucial. Its compromise can lead to unauthorized access. | Store keys securely, use strong key generation practices, and regularly rotate keys. |
| Expiration Times | JWTs should have defined expiration times to prevent long-lived tokens. | Set appropriate expiration times based on the application’s requirements and regularly validate token expiration. |
| Token Revocation | In case of compromised credentials or other security incidents, it’s essential to invalidate tokens. | Implement a token revocation mechanism, such as blacklisting or using additional revocation lists. |
| HTTPS | Always transmit JWTs over HTTPS to protect against interception and tampering. | Enforce HTTPS for all API endpoints handling JWTs. |
| Avoid Sensitive Data | Avoid storing sensitive information directly in JWT payloads. | Use JWTs for authentication and authorization, but rely on other secure methods for sensitive data storage and transmission. |
| JWT Hijacking | Protect against session hijacking by implementing measures like CSRF protection and HTTP-only cookies. | Use CSRF tokens, enforce secure HTTP-only cookies, and consider additional anti-CSRF measures. |
By addressing these security considerations, you can significantly enhance the protection of your JWT-based applications.
4. Common JWT Vulnerabilities
Understanding common JWT vulnerabilities is essential for building secure applications.
| Vulnerability | Description | Mitigation Strategies |
|---|---|---|
| Signature Forgery | An attacker manipulates the JWT’s signature to gain unauthorized access. | Use strong cryptographic algorithms, verify the signature rigorously, and implement additional signature validation checks. |
| Payload Tampering | An attacker modifies the JWT payload to change user claims or permissions. | Use signed JWTs to ensure data integrity. Validate claims on the server-side before granting access. |
| Expiration Time Manipulation | An attacker extends the JWT’s expiration time to maintain unauthorized access. | Enforce strict expiration time checks, consider using short-lived tokens, and implement token revocation mechanisms. |
| Brute Force Attacks | An attacker attempts to guess the secret key or private key through exhaustive trials. | Use strong, complex keys, implement rate limiting, and consider additional authentication factors. |
| Injection Attacks | Malicious code can be injected into the JWT payload, leading to vulnerabilities like XSS or SQL injection. | Validate and sanitize all JWT claims before using them. Implement input validation and output encoding. |
| Information Disclosure | Sensitive information might be inadvertently exposed in the JWT payload. | Avoid including sensitive data in JWTs. Use encrypted tokens or separate channels for sensitive information. |
By understanding these vulnerabilities and implementing appropriate countermeasures, you can significantly enhance the security of your JWT-based applications.
5. Wrapping Up
JSON Web Tokens (JWTs) offer a robust and efficient mechanism for implementing authentication and authorization in modern applications. By understanding their structure, creation, verification, and security implications, you can effectively leverage JWTs to enhance your application’s security and user experience.
While JWTs provide a powerful tool, they are not a silver bullet. Implementing robust security practices, including proper key management, expiration controls, and vulnerability mitigation, is crucial for protecting your application and user data.
