包阅导读总结
1. 关键词:Google Cloud、IAM、Principal、Role、Policy
2. 总结:本文是关于 Google Cloud 中身份配置(IAM)的深入指南,介绍了相关术语,如主体、角色、策略等,并阐述了在实际场景中如何通过角色映射等方式应对 IAM 管理的扩展性挑战。
3. 主要内容:
– 术语介绍
– Principal:在 Google Cloud 中需要访问资源以执行操作的对象,如用户、服务账户等。
– Role:授予资源访问权限的权限集合。
– Policy:附在资源上的角色集合,决定主体对资源的访问权限。
– 管理 IAM
– 初始阶段手动为个人分配权限,团队扩大后管理复杂度增加。
– 利用角色映射解决扩展性挑战,基于岗位职能创建组并为组分配角色。
– 举例说明软件工程师 Varsha 获得访问权限的 IAM 工作流程。
思维导图: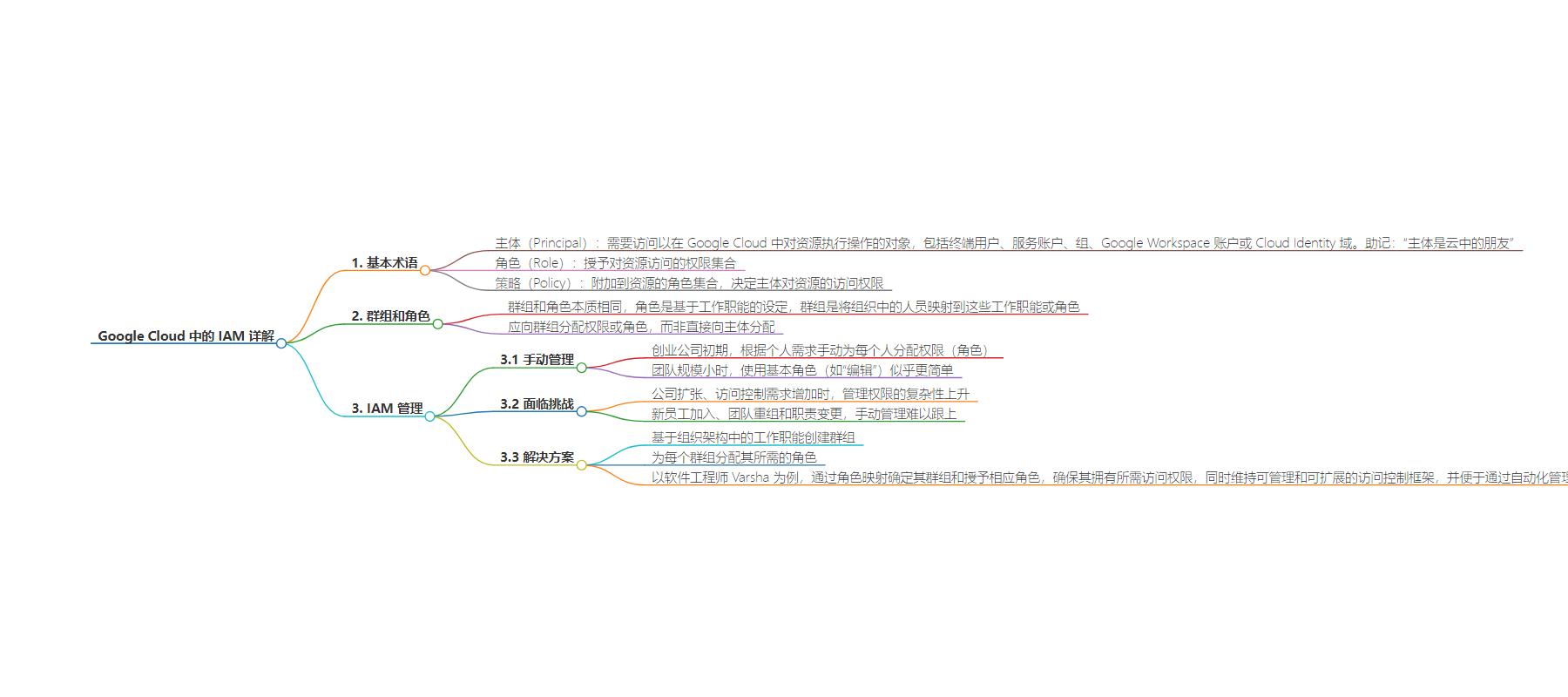
文章来源:cloud.google.com
作者:Sita Lakshmi Sangameswaran,Michele Chubirka
发布时间:2024/7/10 0:00
语言:英文
总字数:1061字
预计阅读时间:5分钟
评分:85分
标签:IAM,Google Cloud,最小权限,职责分离,访问控制
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Let’s review some terminology you’ll need to understand when configuring IAM in Google Cloud.
Principal: Something that needs access to perform an action on a resource in Google Cloud. These objects can be end-user or service accounts, groups, a Google Workspace account, or a Cloud Identity domain that can access a resource. To remember this term, use the mnemonic, “A principal is your pal in the cloud.”
Role: A collection of permissions that grants access to a resource.
Policy: A collection of roles attached to a resource. A policy will allow or deny a principal’s access to a resource.
Remember how we mentioned groups and personas? Fundamentally, these are the same thing. A persona is a job function. For example, you might have a persona called platform engineer or security analyst. These personas then become your groups when you map the humans in your organization to these job functions or personas. This matters because you want to assign permissions or roles to groups, but not directly to principals.
Managing IAM: Staying on top of the mountain
Let’s apply some of these concepts in a real-world scenario. Imagine you’re a platform engineer for a startup. Initially, you manually assign permissions (roles) to each individual based on their needs. Maybe you even use basic roles, because it seems easier to give everyone “editor” rights.
This approach works well when your team is small, but as your company expands and access control requirements increase, so does the complexity of managing all those permissions. New employees join, teams restructure, and responsibilities shift. Manually keeping up with these changes quickly turns into a nightmare, especially when you’re trying to achieve least-privilege and separation of duties.
Persona mapping can help address this scalability challenge with your IAM architecture. Instead of focusing on individual principals, you create groups based on job functions from your org chart. For example, you might have groups for developers, platform engineers, data scientists, and security engineers. Each group is then assigned the roles they need to perform their specific tasks.
By associating roles with groups, you simplify administration and ensure consistent access for users with similar job functions. Consider the scenario where Varsha, a software engineer, needs access to deploy a web application hosted in Google Cloud. With persona mapping, the IAM workflow would look like this:
-
Identify the persona: Varsha is classified as a software engineer for a web application deployed using Cloud Run.
-
Assign the group: Software engineers for this web application are mapped to the “web-app-developer” group.
-
Grant appropriate roles: The “web-app-developer” group is assigned the “Cloud Run Developer role,” providing the necessary read and write access to Cloud Run resources within Google Cloud.
This approach ensures that Varsha and other software engineers have the access they need while maintaining a manageable and scalable access control framework. Additionally, by assigning roles to groups, you create an IAM configuration that is self-documenting and easier to manage through automation.
