包阅导读总结
1. `Terraform 1.9`、`Input Validation`、`String Template Function`、`Enhancements`、`Improvements`
2. HashiCorp 发布了 Terraform 1.9,带来输入变量验证扩展和新的字符串模板函数等新特性及改进,以提高开发者生产力和代码可靠性,还介绍了相关功能和应用示例,并提供了升级指南和鼓励用户反馈。
3.
– Terraform 1.9 发布
– 输入变量验证扩展
– 可参考其他输入变量、数据源和本地值,实现更复杂动态的验证,减少错误和误配置
– 举例说明跨变量引用的验证条件
– 新增“templatestring”函数
– 动态渲染模板,无需保存到本地磁盘
– 举例展示其使用方式
– 现有功能改进
– 优化资源类型的重构
– 允许移除块在资源实例销毁时执行配置器
– 下载和账号相关
– 可下载或注册免费账号
– 提供升级指南和教程
– 社区反馈
– 鼓励用户通过多种渠道反馈,以指导未来开发
思维导图: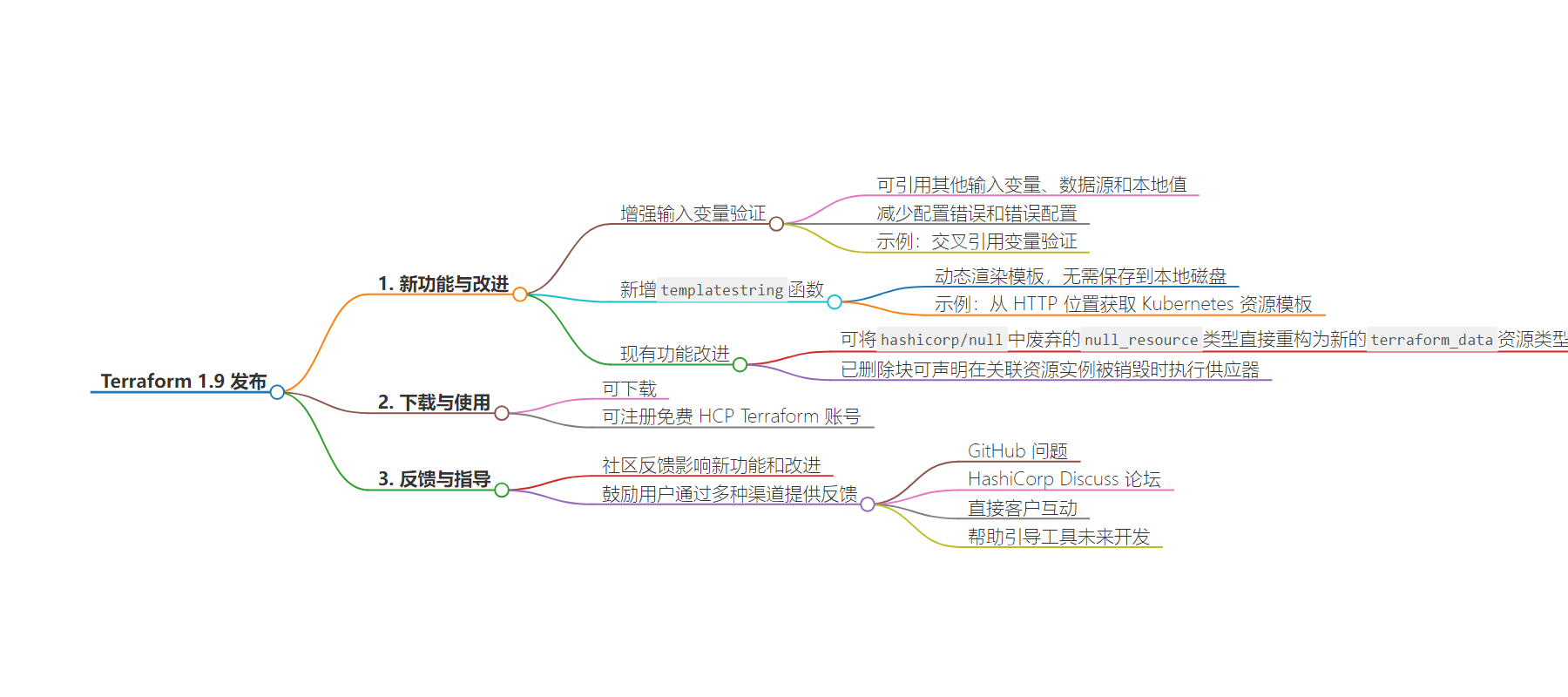
文章来源:infoq.com
作者:Matt Saunders
发布时间:2024/8/9 0:00
语言:英文
总字数:597字
预计阅读时间:3分钟
评分:88分
标签:Terraform,基础设施即代码,HashiCorp,输入验证,字符串模板函数
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
HashiCorp has announced the general availability of Terraform 1.9, introducing several new features and improvements to enhance developer productivity and code reliability. This version of the infrastructure-as-code tool is now available for download and use in HCP Terraform.
One of the key enhancements in Terraform 1.9 is the expansion of input variable validations. This feature, first introduced in Terraform 0.13, allows developers to ensure that input variable values meet specific requirements before execution. Previously, the condition block of an input validation could only refer to the variable itself. With the new release, conditions can now reference other input variables, data sources, and local values, significantly broadening the scope of validation scenarios.
This enhancement enables more complex and dynamic input validations, reducing the likelihood of provisioning errors and misconfigurations caused by invalid or unexpected user input. For example, developers can now create validations that check the relationship between multiple variables or validate input against dynamically retrieved data.
To illustrate this new capability, HashiCorp provided an example where a variable validation condition references the value of a different variable:
/filters:no_upscale()/news/2024/08/terraform-19/en/resources/1Screenshot%20from%202024-08-06%2000-54-11-1722902690900.png)
In this scenario, if a user attempts to execute the Terraform configuration with create_cluster set to false without providing a value for cluster_endpoint, they will encounter a validation error. This cross-referencing validation was previously only possible using precondition blocks on data sources or resources, which could lead to partially completed deployments.
Writing on Medium, Babula Parida explains how this validation can be used.
On X, Mark Tinderholt explains more of the possibilities:
“This thing has the potential to help you validate every nook and cranny from CPU and Memory requirements, Accelerated Networking to Number of supported disks / NICS as well as the ever-murky combinations of supported Virtual Machine / Disk SKUs!!!” – Mark Tinderholt
Tinderholt also announced a Terraform module to make this easy.
Another significant addition in Terraform 1.9 is the new “templatestring” function. This built-in function is designed to render templates obtained dynamically, such as from a data source result, without saving them to a file on the local disk. The function takes two parameters: a direct reference to a named string object in the current module and an object representing the templated variables to interpolate.
This new function is handy for retrieving templates from external locations, transforming them, and passing them to other resources. HashiCorp provided an example demonstrating how to use “templatestring” to retrieve a Kubernetes resource manifest template from an HTTP location, inject input variables and resource references, and then use it in a kubernetes_manifest resource.
Terraform 1.9 also includes improvements to existing features. The deprecated null_resource type in the hashicorp/null provider can now be refactored directly to the new terraform_data resource type using moved blocks. This enhancement builds on the cross-type refactoring feature introduced in Terraform 1.8 and allows developers to modernize their code more easily.
Additionally, removed blocks can now declare provisioners to be executed when the associated resource instances are destroyed. This feature is helpful in scenarios where developers want to remove the resource declaration from their configuration but still execute the destroy-time provisioner.
Users interested in exploring the new features can download Terraform 1.9 or sign up for a free HCP Terraform account. HashiCorp has also provided an upgrade guide for those moving from previous versions and offers hands-on tutorials through HashiCorp Developer.
As with previous releases, HashiCorp acknowledged the role of community feedback in shaping the new features and improvements in Terraform 1.9. The company encouraged users to continue providing feedback through GitHub issues, HashiCorp Discuss forums, and direct customer interactions to help guide future development of the tool.
