包阅导读总结
1. 关键词:NIST、量子计算、加密标准、安全防护、后量子密码学
2. 总结:
– NIST 发布三项加密标准以抵御未来量子计算攻击。
– 尽管量子计算尚处初级阶段,但可能在十年内超越现有技术。
– 这些加密标准基于复杂数学算法,NIST 还在评估其他算法作为备份。
3. 主要内容:
– NIST 为保护政府秘密应对未来强大计算技术的挑战
– 发布三项加密标准:FIPS 203、FIPS 204 和 FIPS 205
– 包括加密算法代码、使用说明及建议
– 量子计算的发展及威胁
– 虽处于初期但可能超越现有服务器集群
– 需提前应对其对传统加密算法的破解
– 后量子密码学
– 基于复杂数学算法,令传统和量子计算机困惑
– 新发布的加密标准:Kyber(FIPS 203)用于通用加密;Dilithium(FIPS 204)用于数字签名;SPHINCS+(FIPS 205)作为数字签名的备份
– 社区讨论
– 专家认为应立即采用新标准加强网络安全
– 强调数据被盗可能未来被解密,需更换加密算法
思维导图: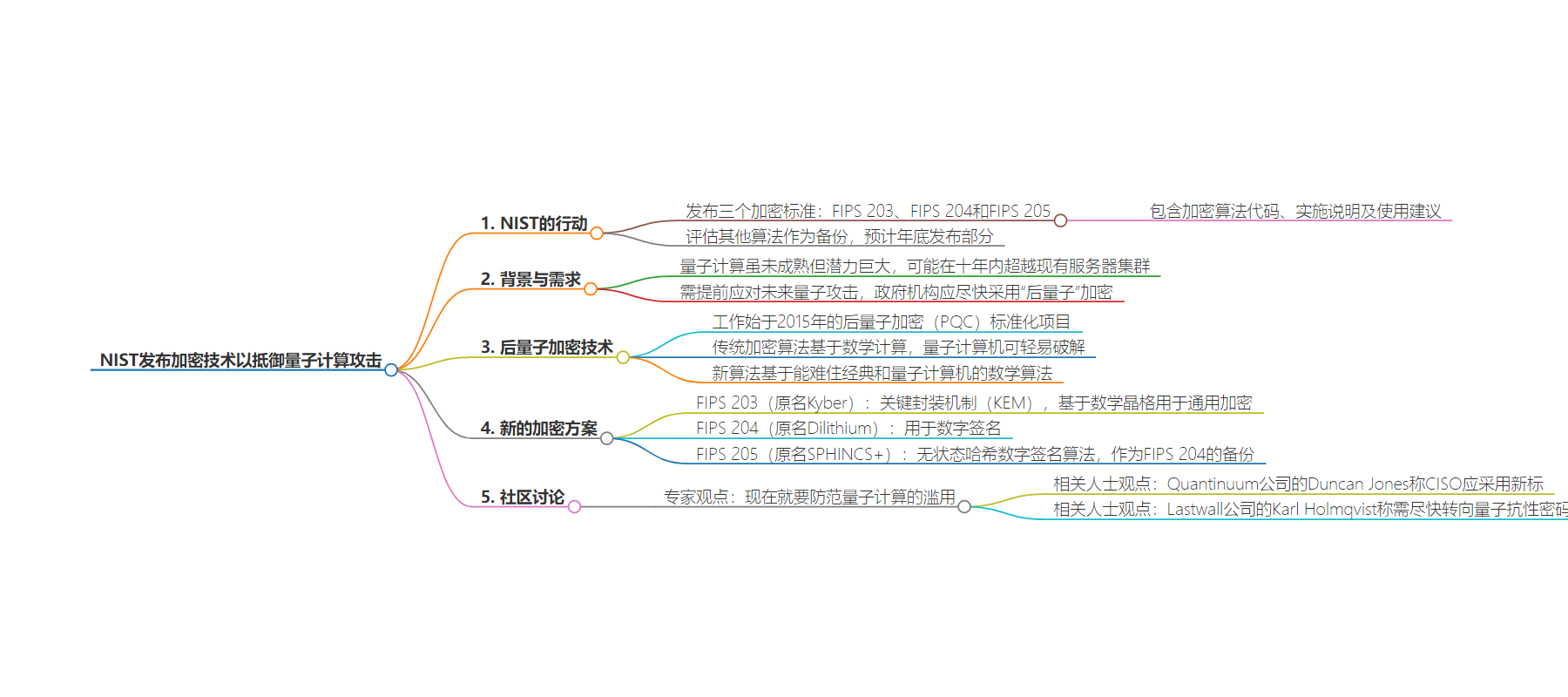
文章地址:https://thenewstack.io/nist-secures-encryption-for-a-time-after-classical-computing/
文章来源:thenewstack.io
作者:Joab Jackson
发布时间:2024/8/16 21:06
语言:英文
总字数:786字
预计阅读时间:4分钟
评分:88分
标签:后量子密码学,量子计算,加密标准,NIST,网络安全
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
How do you secure your secrets against a technology so powerful it hasn’t even been invented yet?
This is the challenge the U.S. National Institute of Standards and Technology took on, in an effort to secure government secrets from tomorrow’s most powerful computing technologies.
On Tuesday, the agency released the first products of this work: three encryption standards guaranteed to be unbreakable, even by tomorrow’s (still non-existent) quantum computers, FIPS 203, FIPS 204 andFIPS 205.
Each of the releases includes the code for the encryption algorithms, along with instructions for how to implement them into security products, and suggestions about how they should be used.
NIST is also evaluating other algorithms to serve as backup, and expects to release a few of those by the end of the year.
Duty Now for the Future
Although quantum computing remains in a nascent stage, it could grow more powerful than today’s largest server clusters. NIST predicts this will happen within the decade.
So you need to secure your stuff today, against quantum attacks of the future, the U.S. federal agency is warning other government agencies. NIST is urging system administrators to start moving to “post-quantum” encryption as soon as possible.
What is Post-Quantum Cryptography?
The three encryption schemes, with more to come, are the work of the agency’s post-quantum cryptography (PQC) standardization project, launched in 2015.
NIST encryption algorithms have formed the basis of modern computing and the internet. They are used to digitally sign documents as well as encrypt data in storage or in transit.
Currently, the Advanced Encryption Standard (AES, FIPS 197), a symmetric block cipher, is the favored approach of NIST for encrypting sensitive data, coming in either 128-, 192- and 256-bit key lengths. AES has largely replaced the Data Encryption Standard (DES), which was offered as 56 bits, and as computer power increased, became more and more easily cracked.
Encryption algorithms have traditionally been built on mathematical calculations that, without they key, would be very difficult for today’s “classical” computers to solve. Typical cryptographic algorithms multiply two very large prime numbers to arrive at a key, a process that would computationally prohibitive to reverse engineer.
Quantum computers, using a still-unfinished set of physics laws that run quantum mechanics, could sift through all the prime numbers with ease, which would render traditional encryption algorithms barely protective of sensitive data.
For this new generation of encryptors, NIST based them on mathematical algorithms that would befuddle both classical and quantum computers.
“The PQC standards rely on the complex mathematics of polynomial lattices and hash functions. Cracking them would be a daunting task for even the most powerful cryptographically relevant quantum computer of the future,” explained IBM in a blog post detailing the new algos. IBM created two of the algorithms and had a hand in developing the third, according to the company.
The New Encryption Schemes
In a bit more detail, the new encryption methods are:
- FIPS 203, formerly known as Kyber, is a key encapsulation mechanism (KEM) called ML-KEM. It will be the primary algorithm for general-purpose encryption. It uses a mathematical lattice to encrypt data, based on the Module Learning with Errors problem.
- FIPS 204, formerly known as Dilithium, will be the primary algorithm for signing digital signatures. It also uses a mathematical lattice problem.
- FIPS 205, formerly SPHINCS+, is a stateless hash-based digital signature algorithm (SLH-DSA), one that uses multiple hashes to encrypt a message. This one will also be used for digital signatures, serving as a backup in case FIPS 204 gets cracked.
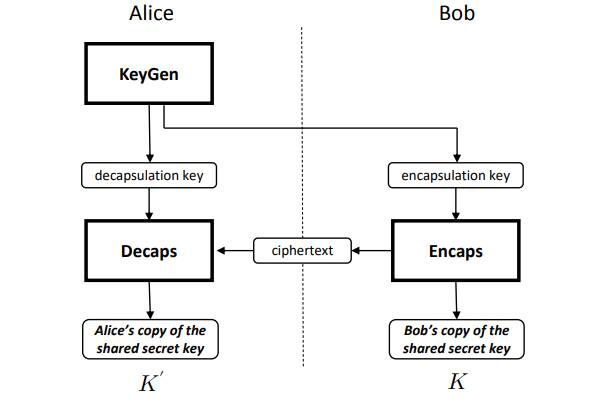
How MEL-KM works (NIST)
Discussion in the Community
While quantum computing remains a concept of the future, the time to guard against its misuse is now, experts noted.
“Every CISO now has a mandate to urgently adopt these new standards alongside other methods for hardening their cybersecurity systems,” wrote Duncan Jones, head of cybersecurity for quantum computing accelerator company Quantinuum, in an e-mail statement.
“We know that data stolen today could be decrypted at any time in the future, and sensitive data such as health records or financial data falling into the wrong hands would be damaging,” Jones wrote.
“We have been warned by the heads of the NSA, the FBI and even the White House that there are active nation-state attacks stealing currently encrypted data and that we need to switch PQC algorithms,” agreed Karl Holmqvist, founder and CEO of security solutions provider Lastwall, in a statement.
“Time is not on our side to change to quantum-resistant ciphers. We need to address this now – it’s time to get to work and eliminate outdated cryptography.”
YOUTUBE.COM/THENEWSTACK
Tech moves fast, don’t miss an episode. Subscribe to our YouTubechannel to stream all our podcasts, interviews, demos, and more.
