包阅导读总结
1. 关键词:Hacktivism、Geopolitics、Nation-States、Vigilance、Strategic Objectives
2. 总结:本文探讨了黑客活动主义的复兴,强调其利用公开形象掩盖真实身份,通过多种方式传播信息,还指出其与地缘政治及国家战略目标的关联,提醒需谨慎分析并保持警惕。
3. 主要内容:
– 利用黑客活动主义策略的行为者借助公开形象掩盖真实身份,并制造公众支持的假象
– 通过直接声明或相关线上资产传播信息
– 攻击中嵌入特定含义,如假信息或大规模 DDoS 活动
– 进行战略定位以获取媒体报道
– 地缘政治驱动的黑客活动主义者常推进国家战略目标
– 部分可能独立运作,部分与国家支持的网络间谍组织有关
– 一些国家赞助的行为者利用黑客活动主义形象进行掩护活动
– 举例说明相关情况,如俄罗斯、伊朗、朝鲜等国家相关事件
– 存在看似独立但受国家政治影响的黑客活动主义团体
– 如立陶宛与俄罗斯相关事件及中东长期存在的相关活动
思维导图: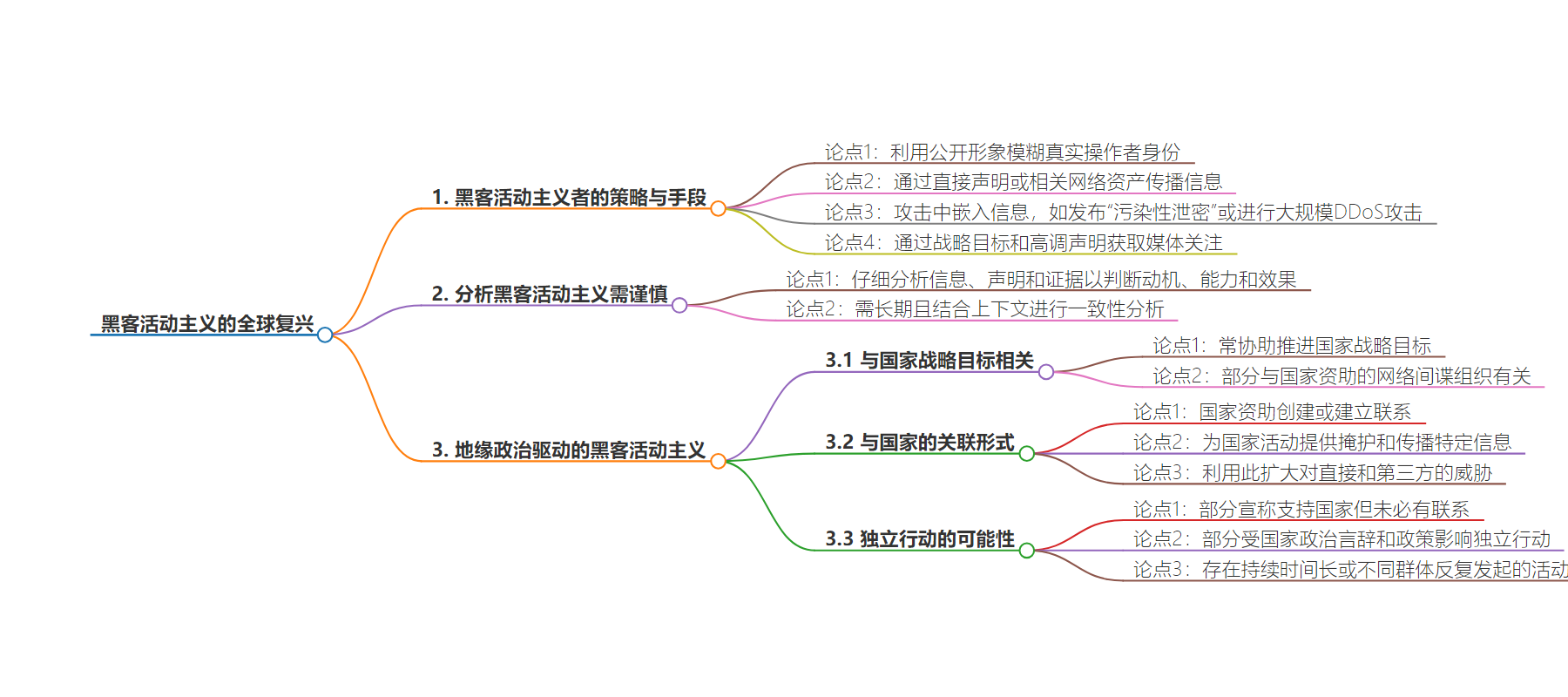
文章地址:https://cloud.google.com/blog/topics/threat-intelligence/global-revival-of-hacktivism/
文章来源:cloud.google.com
作者:Mandiant
发布时间:2024/6/27 0:00
语言:英文
总字数:2482字
预计阅读时间:10分钟
评分:88分
标签:威胁情报,黑客行动主义,网络安全,风险评估
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Actors leveraging hacktivist tactics use overt personas to obfuscate the identity of their real operators and, in some cases, to generate the impression of organic public support for a given issue or event.
The hacktivist personas promote their messaging most often via direct claims or to persona-affiliated online assets such as on social media or actor-owned sites. The meaning can also be embedded in the attack itself, for instance, via the distribution of “tainted leaks” that feature altered or false information or conducting massive DDoS campaigns in parallel to geopolitical or cultural events. Strategic targeting and other high-profile claims also help groups increase the likelihood of receiving mainstream media coverage.
Mandiant emphasizes the importance of carefully analyzing groups’ messaging, claims, and any independent evidence available before drawing conclusions about an actor’s motivation, capability, or efficacy, since hacktivist tactics incentivize such actors to inflate the impact of their actions and make otherwise inaccurate or wholesale fabricated claims. A proper understanding of hacktivist personas and the impact of their actions requires consistent analysis over time and in context of communications with other actors. In some cases, obtaining conclusive evidence is not possible.
Geopolitically Motivated Hacktivists Often Advance Strategic Objectives from Nation-States
Given the inherent overlap between components of hacktivist tactics and information operations, geopolitically motivated hacktivist actors often help advance strategic objectives from nation-states. Although in most cases the hacktivists likely operate independently, we have also uncovered recent instances of actors with strong links to state-sponsored cyber espionage groups.
Geopolitically Motivated Hacktivists Linked with Nation-States
Some nation-state-sponsored actors have created hacktivist cutouts or established links with hacktivist personas as a front for their own activities. Hacktivist personas provide such actors with a mechanism to spread messaging that would otherwise be covert action but with a veil of plausible deniability for their cyber threat activity. In such cases, hacktivist messaging can help to draw attention to specific narratives or even influence real life events resulting in physical consequences, while the plausible deniability from using these cutouts expands the threat to both direct and third parties associated with any given event or issue. Hacktivist personas also offer well-resourced actors the ability to develop and/or leverage persistent assets and hacktivist brands that increase the likelihood of their messaging reaching the desired target audiences.
- In 2024 we released a report describing how Russian military group APT44 (also commonly known as Sandworm, FROZENBARENTS, and Seashell Blizzard) cultivated hacktivist personas as assets to claim responsibility for a series of wartime disruptive operations and to amplify the narrative of successful disruption.
- Public sources have also indicated nation-state sponsorship for hacktivist groups such as pro-Iran CyberAv3ngers, which the U.S. government has linked to the Islamic Revolutionary Guard Corps (IRGC) and pro-Israel “Gonjeshke Darande” (Predatory Sparrow), which the Iranian government has attributed to Israel.
- As early as 2014, an iconic attack targeting Sony Pictures Entertainment illustrated nation-states’ leveraging of hacktivist brands to engage in cyber threat activity. The attack, in which a false hacktivist front called Guardians of Peace (#GOP) wiped Sony’s infrastructure and leaked a large volume of proprietary information, was attributed by the U.S. Federal Bureau of Investigation (FBI) to the North Korean government.
Geopolitically Motivated Hacktivists That Likely Act Independently
Although many of the recently active high-profile hacktivist groups we track explicitly describe their activity as supporting the interests of a nation-state, these pledges of allegiance do not necessarily mean that all such groups are linked to nation-states. We have also recurrently observed hacktivist groups that appear to act independently, but guide their operations with interpretations of the political rhetoric and policy objectives communicated from the leaders of the nation-state or political groups they support. In this case, while the threat activity may not be directed by national leadership, it still serves to advance its specific objectives.
- For example, on June 18, 2022, Lithuania imposed a ban on the rail transit of goods subject to European sanctions to the Russian far-western exclave of Kaliningrad. Following the imposed ban, pro-Russian hacktivist groups announced attacks on Lithuanian entities across multiple sectors after Russian leadership warned there would be consequences from Lithuania’s action. The attacks continued until both countries reached a consensus.
- In some instances, we have observed campaigns that can last for extended durations or be revived by different groups over time. Such is the case of repetitive spikes in hacktivist activity that we often observe in the Middle East associated with holidays such as Quds Day or the recurrent #OpIsrael, which has grown since at least 2013 to involve all sorts of hacktivist activity targeting Israel every year.
