包阅导读总结
1. `API 安全风险、协同防御、组织职能、安全策略、协作文化`
2. 本文探讨了在云计算时代 API 安全的重要性,强调组织需建立协同防御体系来应对 API 安全风险,涉及各职能团队的责任及协作文化的培养。
3.
– 背景
– 云计算时代,API 是现代应用关键,组织依赖其提供服务,保障其安全至关重要。
– 黑客利用漏洞攻击,数字化和连接性增加带来安全威胁。
– 协同防御
– API 增长吸引攻击者,漏洞危害严重,需多部门协同建立安全系统。
– 产品团队/开发者:采用安全编码,设计开发时融入安全特性。
– 安全团队:定义安全策略,进行扫描、测试、建模等。
– IT 运营/DevOps:确保基础设施配置部署,管理访问控制等。
– 业务利益相关者:评估风险,分配资源,确保安全与业务一致。
– 其他团队:也发挥重要作用。
– 协作关键
– 培养协作文化,共享安全责任。
– 包括定期沟通、建立集中知识库、开展培训等关键步骤。
思维导图: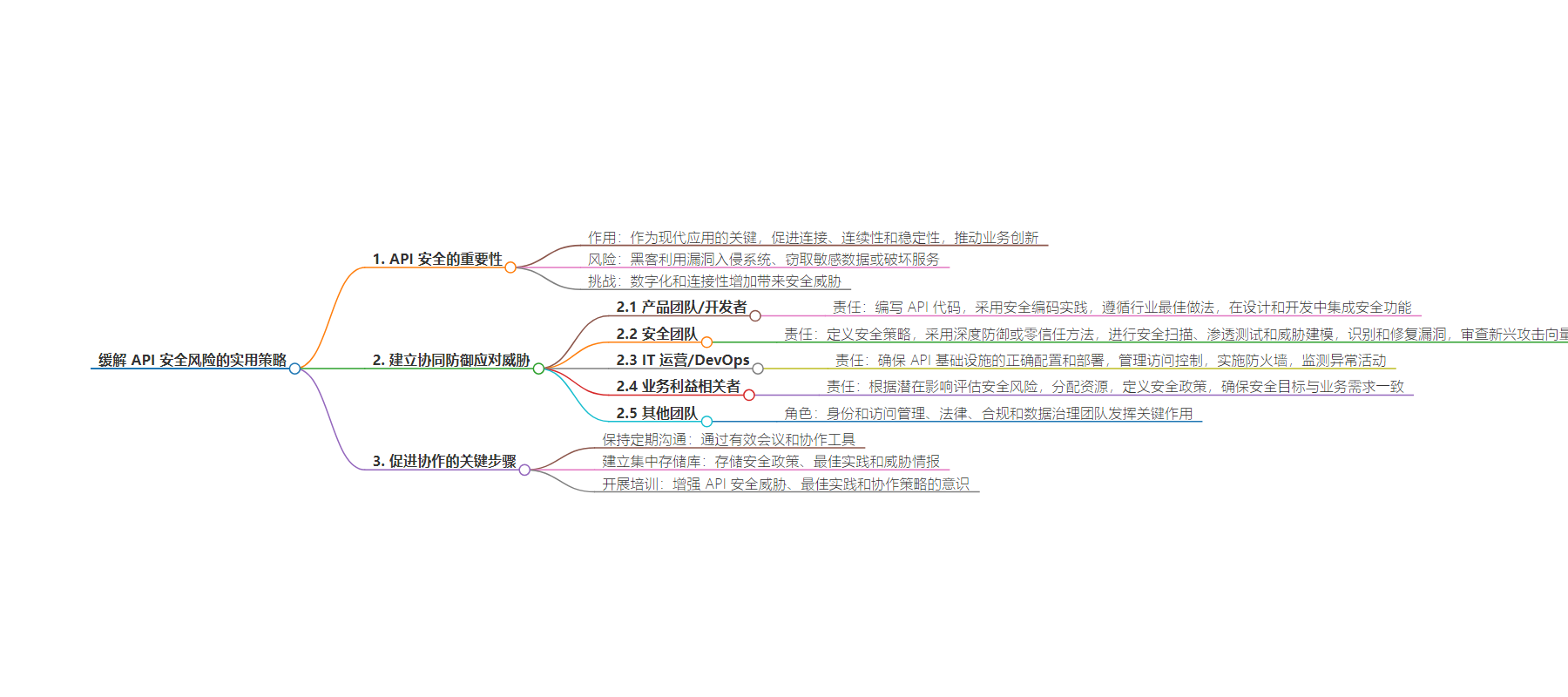
文章来源:infoworld.com
作者:InfoWorld
发布时间:2024/8/12 8:30
语言:英文
总字数:960字
预计阅读时间:4分钟
评分:88分
标签:API 安全,协作,身份和访问管理,AI 在安全中的应用,网络安全
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
In our era of cloud computing, distributed applications, and loosely coupled microservices, application programming interfaces (APIs) serve as the lynchpins of modern applications, facilitating connectivity, continuity, and stability while enabling continuous business innovation. As organizations rely on APIs for core services, securing them is critical. Hackers exploit vulnerabilities to infiltrate systems, steal sensitive data, or disrupt services. Increased digitization and connectivity expose organizations to security threats. Therefore, a coordinated approach is essential to managing operational and information technology systems effectively, ensuring protection against such attacks.
Building a collaborative defense against evolving threats
The exponential growth of APIs has expanded the digital landscape, enticing attackers to exploit vulnerabilities, gaining unauthorized access to confidential information or disrupting critical services. The implications of an API breach can be severe, causing financial losses and damaging an organization’s reputation. Addressing these threats requires a concerted effort involving various organizational functions to establish an effective API security system.
- Product teams/developers: Responsible for crafting API code, they must embrace secure coding practices, adhere to industry best practices, and integrate security features during design and development.
- Security teams: Define security policies advocating a defense-in-depth or zero-trust approach. They conduct regular security scans, penetration testing, and threat modeling, identifying and remedying vulnerabilities and reviewing emerging attack vectors.
- IT operations/devops: Ensure proper configuration and deployment of infrastructure for APIs, manage access controls, implement firewalls, and monitor for unusual activity.
- Business stakeholders: Assess security risks based on their potential impact on the organization. They allocate resources, help define security policies, and ensure alignment between security objectives and business imperatives.
- Other teams: Identity and access management, legal, compliance, and data governance teams also play crucial roles.
Fostering collaboration is crucial for a cohesive defense strategy, emphasizing a culture of shared responsibility where security is a priority for everyone. Key steps include maintaining regular communication among stakeholders through efficient meetings and collaboration tools, establishing a centralized repository for security policies, best practices, and threat intelligence, and conducting training sessions on API security threats, best practices, and collaboration strategies to enhance awareness.
