包阅导读总结
1. `Cloudflare`、`Application Security Report`、`DDoS Attacks`、`CVE Exploits`、`Malicious Traffic`
2. Cloudflare 发布 2024 应用安全报告,指出恶意流量增加,DDoS 攻击仍是主要攻击向量,CVE 利用速度快,零日漏洞增多。报告还介绍了新的客户端安全部分,分析了第三方库风险等。
3.
– Cloudflare 发布 2024 应用安全报告
– 关键发现:恶意流量因地缘政治和选举季增加
– 新内容:引入客户端安全部分
– 攻击情况
– DDoS 攻击仍是头号攻击向量
– CVE 攻击利用迅速
– 流量处理
– HTTP 请求和 DNS 查询处理量增加
– 机器人情况
– 多数机器人未经验证且可能恶意
– 不同组织对“坏”机器人标准不同
– 漏洞情况
– 零日漏洞上升,披露的 CVE 增多
– 第三方库风险:分析了相关风险及主要提供者
– 报告获取:PDF 格式和 Cloudflare Radar 可获取
思维导图: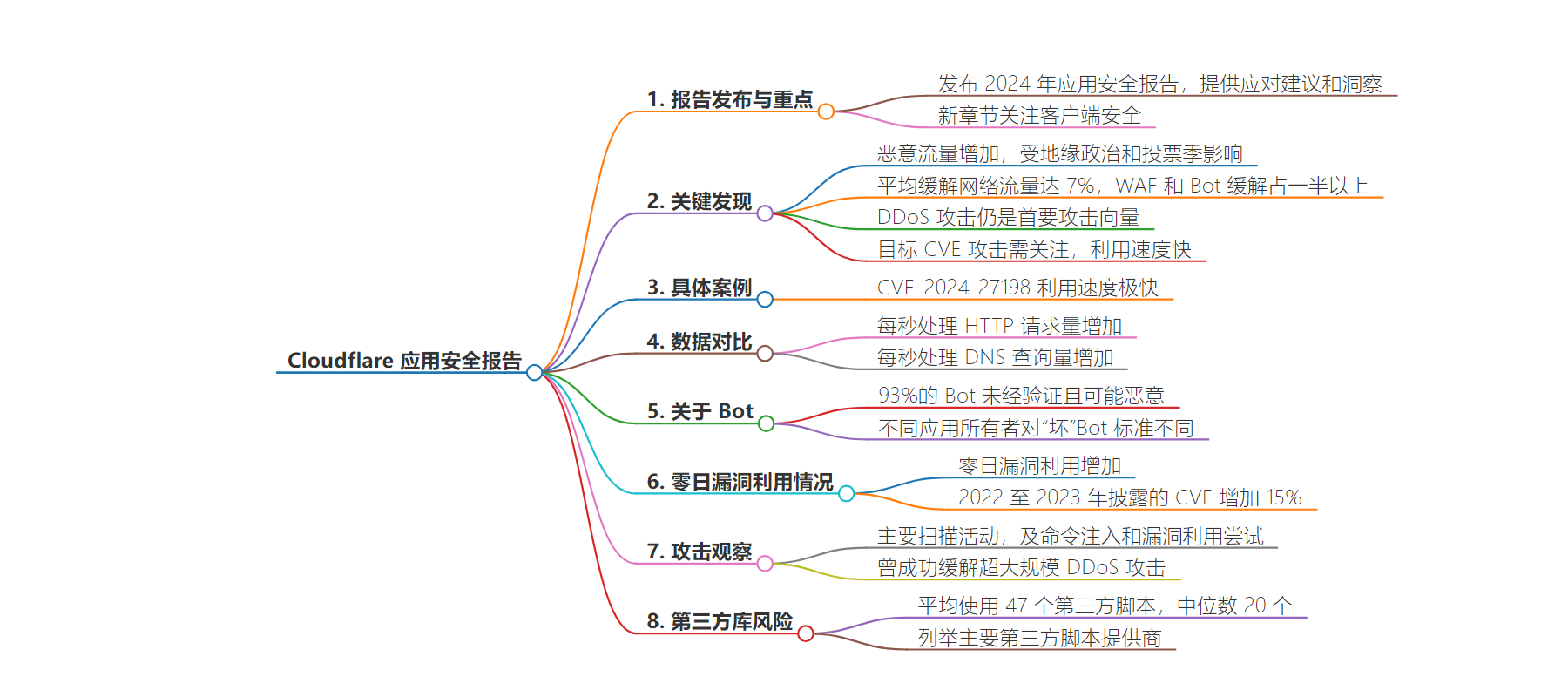
文章来源:infoq.com
作者:Renato Losio
发布时间:2024/7/31 0:00
语言:英文
总字数:564字
预计阅读时间:3分钟
评分:87分
标签:应用程序安全,DDoS 攻击,CVE 利用,Cloudflare,Web 应用程序安全
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Cloudflare recently released its 2024 Application Security Report, offering recommendations and insights on addressing many raised concerns. A key finding of the report is the increase in malicious traffic, driven by geopolitical events and voting seasons.
Now in its fourth edition, the Application Security Report introduces a new section focused on client-side security within the context of web applications. Michael Tremante, senior director of product at Cloudflare, Sabina Zejnilovic, data scientist at Cloudflare, and Catherine Newcomb, product marketing manager at Cloudflare, summarize:
From a global standpoint, mitigated traffic across the whole network now averages 7%, and WAF and Bot mitigations are the source of over half of that. While DDoS attacks remain the number one attack vector used against web applications, targeted CVE attacks are also worth keeping an eye on, as we have seen exploits as fast as 22 minutes after a proof of concept was released.
/filters:no_upscale()/news/2024/07/cloudflare-application-security/en/resources/1unnamed--5--3-1721640125077.png)
Mitigated traffic by Cloudflare product group. Source: Cloudflare blog
The speed of exploitation of disclosed CVEs can be faster than the speed at which humans can create WAF rules. For example, exploitation attempts of CVE-2024-27198 (JetBrains TeamCity authentication bypass) were observed only 22 minutes after the proof-of-concept code was published.
/filters:no_upscale()/news/2024/07/cloudflare-application-security/en/resources/1image8-2-1721640154254.png)
JetBrains TeamCity authentication bypass timeline. Source: Cloudflare blog
Comparing the latest two reports, Cloudflare now processes 57 million HTTP requests per second, a 23.9% increase year-over-year (YoY), with peaks reaching 77 million requests per second, a 22.2% increase YoY. Additionally, Cloudflare handles 35 million DNS queries per second, including both authoritative and resolver requests, marking a 40% increase YoY. Akira Brand, application security specialist, comments:
I enjoyed reading the “Application Security Report 2024” this morning. My key takeaway? Bots! 93% of bots are unverified and potentially malicious. That’s a lot of unknown activity on your applications!
Tremante, Zejnilovic, and Newcomb explain why only a fraction are verified bots and warn:
Different application owners may have different criteria for what they deem a “bad” bot. For example, some organizations may want to block a content scraping bot that is being deployed by a competitor to undercut on prices, whereas an organization that does not sell products or services may not be as concerned with content scraping.
According to the report, zero-day exploits are rising, with 97 exploited in 2023 alongside a 15% increase in disclosed CVEs from 2022 to 2023. Cloudflare observed mostly scanning activities, followed by command injections and exploitation attempts of vulnerabilities with available PoCs, including Apache, Coldfusion, and MobileIron CVEs.
As previously reported on InfoQ, in August 2023, Cloudflare and other providers mitigated a hyper-volumetric HTTP/2 Rapid Reset DDoS attack three times larger than any previously observed. Andrés-Leonardo Martínez-Ortiz, machine learning SRE at Google, comments:
The 2024 Cloudflare Application Security Report reveals a dramatically changed Internet security landscape. Increased malicious traffic, driven by geopolitical events and active voting seasons, necessitates a closer look at application security.
Using data from Page Shield, Cloudflare’s client-side security product, the authors analyze third-party libraries and the risks they pose to organizations, such as the recent Polyfill.io supply chain attack reported on InfoQ. According to the report, Cloudflare’s typical enterprise customer uses an average of 47 third-party scripts, with a median of 20 third-party scripts. Google (Tag Manager, Analytics, Ads, Translate, reCAPTCHA, YouTube), Meta (Facebook Pixel, Instagram), and Cloudflare (Web Analytics) are the top third-party script providers.
The full report is available in PDF format and on Cloudflare Radar.
