包阅导读总结
1. 关键词:Android 应用安全、漏洞检测、安全知识库、修复指南、安全生态
2. 总结:本文介绍了谷歌如何帮助开发者修复 Android 应用中的漏洞,包括对应用的漏洞扫描,以及推出的 Android 应用安全知识库(AAKB),提供修复指导和预防建议,以建立更安全的 Android 生态。
3. 主要内容:
– 漏洞检测
– 谷歌扫描 Google Play 上的每个应用,检测常见安全漏洞类别。
– 发现问题通知开发者,严重未修复的可能被下架。
– Android 应用安全知识库(AAKB)
– 目的是为编写安全的 Android 软件建立指南。
– 是常见代码问题的存储库,含修复示例和解释。
– 数据用于改进指导,使 Android 生态默认更安全。
– 工作机制
– 建立清晰的指导和代码示例,与 OWASP MASVS 标准对齐。
– 通过 AAKB 主页和 Android Studio 提供指导。
– Android Studio 内现有安全检查更新描述含 AAKB 链接,开源安全检查含点击修复功能和 AAKB 链接。
思维导图: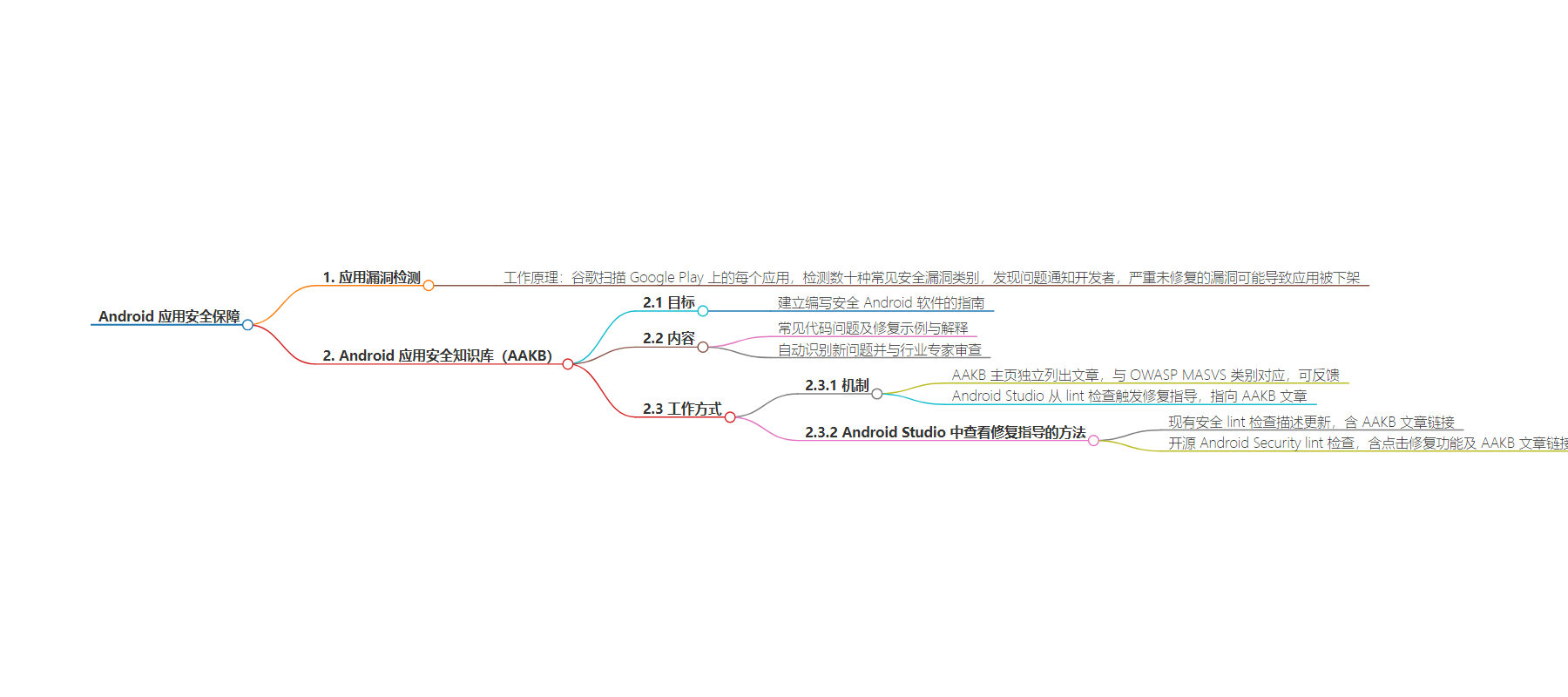
文章地址:http://android-developers.googleblog.com/2024/07/making-security-easy-vuln-remediation.html
文章来源:android-developers.googleblog.com
作者:Android Developers
发布时间:2024/7/25 16:00
语言:英文
总字数:720字
预计阅读时间:3分钟
评分:91分
标签:Android 安全,漏洞修复,AAKB,Android Studio,OWASP MASVS
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Posted by Bessie Jiang – Software Engineer and Chris Schneider – Security Engineer
Contributors: Maciej Szawłowski – Security Engineer, Hannah Barnes – Technical Program Manager, Dirk Göhmann – Technical Writer, Patrick Mutchler – Software Engineer
Security is tricky, but vital to protecting your users and their data. We’re here to help you build secure Android apps with fewer vulnerabilities for an even safer Android ecosystem for everybody.
Vulnerability Detection – How it Works
Google currently scans every app on Google Play for dozens of common security vulnerability classes. If we spot something, we let you know so you can fix the problem. Imagine a pentesting team hunting for bugs in each of the millions of apps published on Play, rooting out issues like bad TLS configurations that expose network traffic or directory traversal vulnerabilities that let adversaries read from or write to an app’s private files.
We are committed to keeping our joint users protected. In serious cases, if a security vulnerability doesn’t get fixed, Google may remove the app from Google Play to keep users safe.
Android Application Security Knowledge Base
We know that it isn’t always enough to just tell you about a vulnerability in your app; you need to know how to fix the issue and how to prevent similar issues from cropping up in the future. To this end, we are introducing our security guidance and recommendations under a new program: the Android Application Security Knowledge Base (AAKB).
AAKB aims to establish guidelines for writing secure Android software. It is a repository of common code issues, with remediation examples and explanations for implementing specific code patterns. Organic in nature, new issues are identified automatically for review with experts across the industry – ensuring broad but well-tested approaches and guidance.
Data collected from your engagement with AAKB is used to improve guidance, and to identify how to make the Android ecosystem more secure by default.
How Does it Work?
AAKB establishes clear, vetted guidance with code examples. Guidance is aligned to OWASP MASVS standards, and content is vetted in partnership with technical peers, such as Microsoft. This helps ensure the content is not biased to one party and represents state-of-the-art standards. This also provides an educational place for you to proactively remediate security risks in your applications using industry-wide standards, with direct access to knowledge from subject-matter experts.
The guidance is available through two mechanisms:
The AAKB homepage lists each article independently, aligned to the relevant OWASP MASVS category (e.g. MASVS-STORAGE). Anyone can view or provide direct feedback to this content. Security is an ever-changing field, and being able to update guidance on the fly means software development lifecycles can be updated dynamically with as little friction as possible.
Android Studio triggers remediation guidance from lint checks by pointing directly to AAKB articles. You can fix problems as you’re building the app and before they ever reach users.
There are two methods to view remediation guidance with Android Studio:
Existing security lint checks within Android Studio Giraffe+ have had their descriptions updated to include a link to the relevant AAKB article, allowing you get more context as to why a particular code snippet might be potentially “at-risk”.
Meanwhile, the open-source Android Security lint checks give you access to our most recent guidance and experiments to further protect your mobile applications and get ahead of future security concerns.
Add the open source checks to your project by following the README. These lint checks all contain click-to-fix functionality that make it easy for you to write safer code with minimal effort, as well as links to the relevant AAKB articles like the built-in IDE checks.
All built-in IDE lint checks can be found in this list, with many under the Security category containing links to relevant AAKB articles. We would love to hear your feedback and suggestions for new lint checks and other improvements to the open-source lint library.
