包阅导读总结
1. 关键词:Elastic Cloud、Encryption、AWS KMS、BYOK、Enterprise
2. 总结:文本主要介绍了在 Elastic Cloud 中使用 AWS KMS 进行静态加密时的自带密钥(BYOK)相关内容,包括获取自己控制的密钥、升级到企业订阅级别可用 BYOK 及注意事项,还提到了访问控制和自定义快照存储库的加密情况。
3. 主要内容:
– 静态加密在 Elastic Cloud 中使用 AWS KMS 的 BYOK
– 获取自己的密钥
– 在 AWS KMS 账户中设置,创建对称单区域或多区域副本密钥,需在有部署的每个区域可用,可用于多个部署,但安全最佳实践建议每个部署使用不同密钥
– 升级到企业订阅级别可用 BYOK,其他云提供商后续会有此功能
– 访问控制
– 创建 AWS IAM 策略控制对 Elastic 集群的访问
– 注意事项
– 使用自定义快照库时,快照不会自动用密钥加密,但文件系统仍会加密存储在磁盘上的数据
思维导图: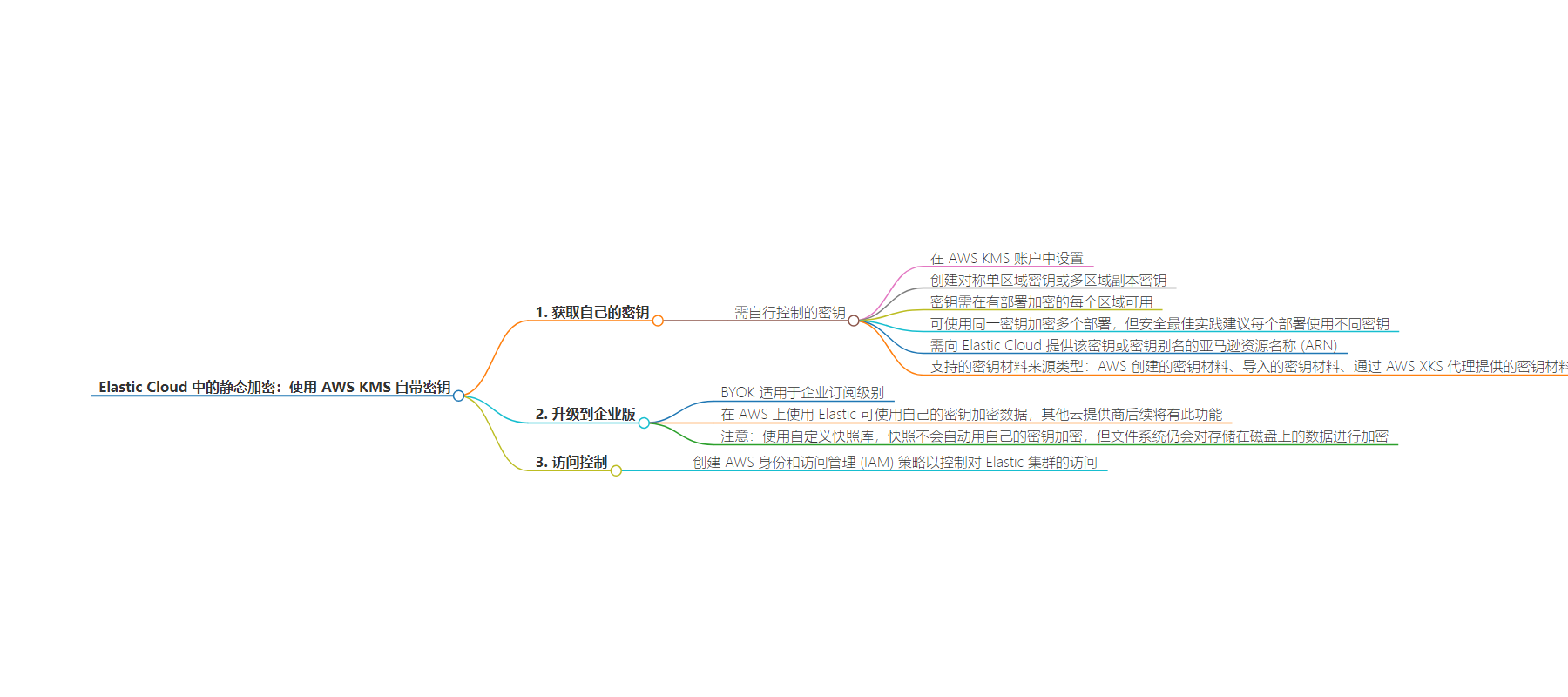
文章地址:https://www.elastic.co/blog/encryption-at-rest-elastic-cloud-aws-kms
文章来源:elastic.co
作者:Jonathan Simon,Udayasimha Theepireddy (Uday)
发布时间:2024/8/2 17:39
语言:英文
总字数:1130字
预计阅读时间:5分钟
评分:87分
标签:静止数据加密,AWS KMS,Elastic Cloud,数据安全,云安全
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
1. Get your own key: To use BYOK, you need a key that you control. You set this up in your AWS KMS account. Create a symmetric single-region key or multi-region replica key. The key must be available in each region in which you have deployments to encrypt. You can use the same key to encrypt multiple deployments, although security best practices recommend using a different one per deployment. Later, you will need to provide the Amazon Resource Name (ARN) of that key or key alias to Elastic Cloud. We currently support the following key material origin types:
-
KMS: AWS Created Key Material
-
External: Imported Key Material
-
External Key Store (XKS): Key Material Provided Via AWS XKS Proxy
2. Upgrade to Enterprise: BYOK is available for the Enterprise subscription level. This means if you’re using Elastic on AWS, you can encrypt your data using your own key. Other cloud providers will have this feature later on.
Keep in mind: If you’re using a custom snapshot repository instead of Elastic Cloud’s default one, your snapshots won’t automatically be encrypted with your key. However, the file system itself will still encrypt data being stored on disk.
3. Access control: Create AWS Identity and Access Management (IAM) policies to control access to the Elastic cluster.
