包阅导读总结
1. 关键词:Grafana SSO、认证方法、优势、配置更新、最佳实践
2. 总结:本文介绍了 Grafana SSO,包括与其他认证方法的比较、优势、配置更新及设置的最佳实践,并提到了故障排除的要点。
3. 主要内容:
– Grafana 从数据可视化平台发展为全功能可观测性平台
– 比较了 Grafana 支持的认证方法,如 LDAP、基本认证、JWT 认证、SSO 等,包括描述、安全级别、用户管理、设置难易度和可扩展性
– 阐述了使用 Grafana SSO 的原因,如增强安全性和提供更好的用户体验
– 介绍了 Grafana SSO 配置的新变化,如新 UI 配置、API 支持、Terraform 集成等
– 解释了配置文件与 UI/API 的特点及选择建议
– 给出了设置 Grafana SSO 的最佳实践,如了解身份提供者、正确配置重定向 URI 等
– 提供了 SSO 设置故障排除的方法和基础要点
思维导图: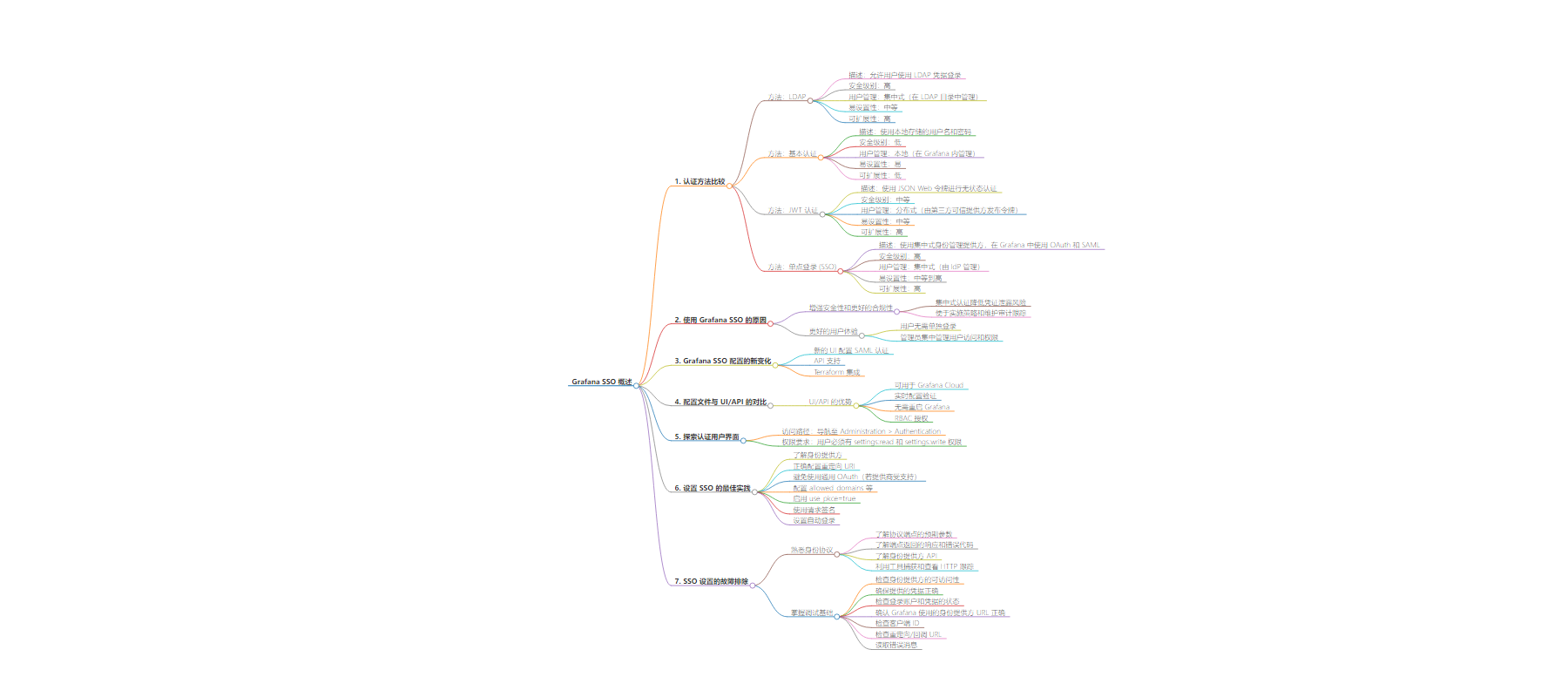
文章来源:grafana.com
作者:Vardan Torosyan
发布时间:2024/7/31 13:23
语言:英文
总字数:1636字
预计阅读时间:7分钟
评分:90分
标签:Grafana,单点登录,身份验证,安全,用户管理
以下为原文内容
本内容来源于用户推荐转载,旨在分享知识与观点,如有侵权请联系删除 联系邮箱 media@ilingban.com
Grafana began as an open and composable platform for data visualization. Today, Grafana has evolved into an all-in-one observability platform, providing everything from infrastructure and application performance monitoring to load testing and incident response.
As organizations extend their use of Grafana, efficient and secure authentication and authorization is essential. Fortunately, Grafana provides multiple ways to authenticate users, including
In this post, we’ll provide an overview of Grafana SSO, including how it compares to other authentication methods, its benefits, and recent updates that make it easier to configure SSO in your environment.
A comparison of authentication methods
Before we dive into the details of SSO, specifically, let’s compare the supported authentication methods in Grafana. Note: For more information on which methods are supported in Grafana OSS, Grafana Cloud, and Grafana Enterprise, please refer to our technical documentation.
| Method | LDAP | Basic authentication | JWT authentication | Single sign-on (SSO) |
| Description | Allows users to login with their LDAP credentials | Uses username and password stored locally | Uses JSON Web Tokens for stateless authentication. Allows Grafana to accept a JWT token provided in the HTTP header. | Allows for the use of a centralized identity management provider, using OAuth and SAML in Grafana. Built-in support for multiple known identity providers (IdPs), as well as support for setting up Generic OAuth. |
| Security level | High (centralized and managed externally) | Low (depends on password strength, user input) | Moderate (in certain configurations can lead to the token being exposed – for example, in logs – which leaves room for hijacking) | High (centralized and managed by the IdP, and allows for the implementation of multi-factor authentication on the IdP side) |
| User management | Centralized (managed in LDAP directory) | Local (managed within Grafana) | Distributed (tokens issued by third-party trusted provider) | Centralized (managed by the IdP) |
| Ease of setup | Moderate (requires LDAP server and configuration) | Easy (built-in, minimal setup) | Moderate (requires token generation, validation, and ensuring security) | Moderate to high (depends on the IdP and protocol used) |
| Scalability | High (suitable for large organizations) | Low (best for smaller setups, or testing) | High (scales well with stateless tokens) | High (ideal for large organizations with multiple services) |
Additionally, you can configure Grafana to use Anonymous authentication, which allows users to access Grafana without requiring any login.
Ultimately, your choice of authentication type depends on your organization’s unique requirements. Most of these authentication methods also allow you to sync user permissions from external providers to Grafana and, therefore, easily control access. While this is beyond the scope of this blog post, you can read more in our technical documentation.
Why use SSO with Grafana?
While SSO might not be applicable to all types of organizations and users, it comes with several advantages compared to other forms of authentication, including:
- Enhanced security and better compliance: Centralized authentication reduces the risk of compromised credentials. It makes it easier to enforce policies and maintain audit trails, and also scales really well.
- Better user experience: Users can access Grafana resources without needing to log in separately (aka, no password fatigue), and administrators can manage user access and permissions from a centralized place (for example, their IdP).
What’s new in Grafana SSO configuration?
Historically, configuring SSO in Grafana required updating static configuration files and restarting the Grafana instance for the changes to take effect. This process could be cumbersome and disruptive.
With the Grafana 10 release, we introduced a new UI to easily configure SAML authentication. Thanks to feedback from our community, we decided to streamline the entire SSO setup process and introduced the following updates, starting with Grafana 11:
- UI configuration: Configure SSO directly through the Grafana user interface.
- API support: Automate SSO setup and management using Grafana’s API. Refer to the documentation for more information.
- Terraform integration: Manage SSO configurations as code with Terraform support. Refer to the documentation for more information.
Configuration files vs. the UI/API
Configuring SSO through Grafana configuration files is still supported and might be applicable in certain scenarios, including when there’s limited infrastructure automation. That said, using the UI or API instead of configuration files has the following advantages:
- Available in Grafana Cloud: Set up SSO inside of your Grafana Cloud instance without needing to file a support request.
- Real-time configuration validation: When using the UI or API, all settings are validated in real time, providing immediate feedback on the validity of the configuration.
- No need to restart Grafana: Using the UI or API eliminates the need to restart Grafana after making changes.
- RBAC authorization: You have the flexibility to authorize specific users to access the UI or API by using role-based access control (RBAC).
It is not recommended to mix configuration methods (for example, to define some fields in a config file and some through the API). If, for some reason, configuration has to be done using both options, Grafana will follow a specific precedence order when loading the configuration:
- Settings that were configured using the UI/API, or Terraform.
- Settings from environment variables.
- Settings from the Grafana configuration file.
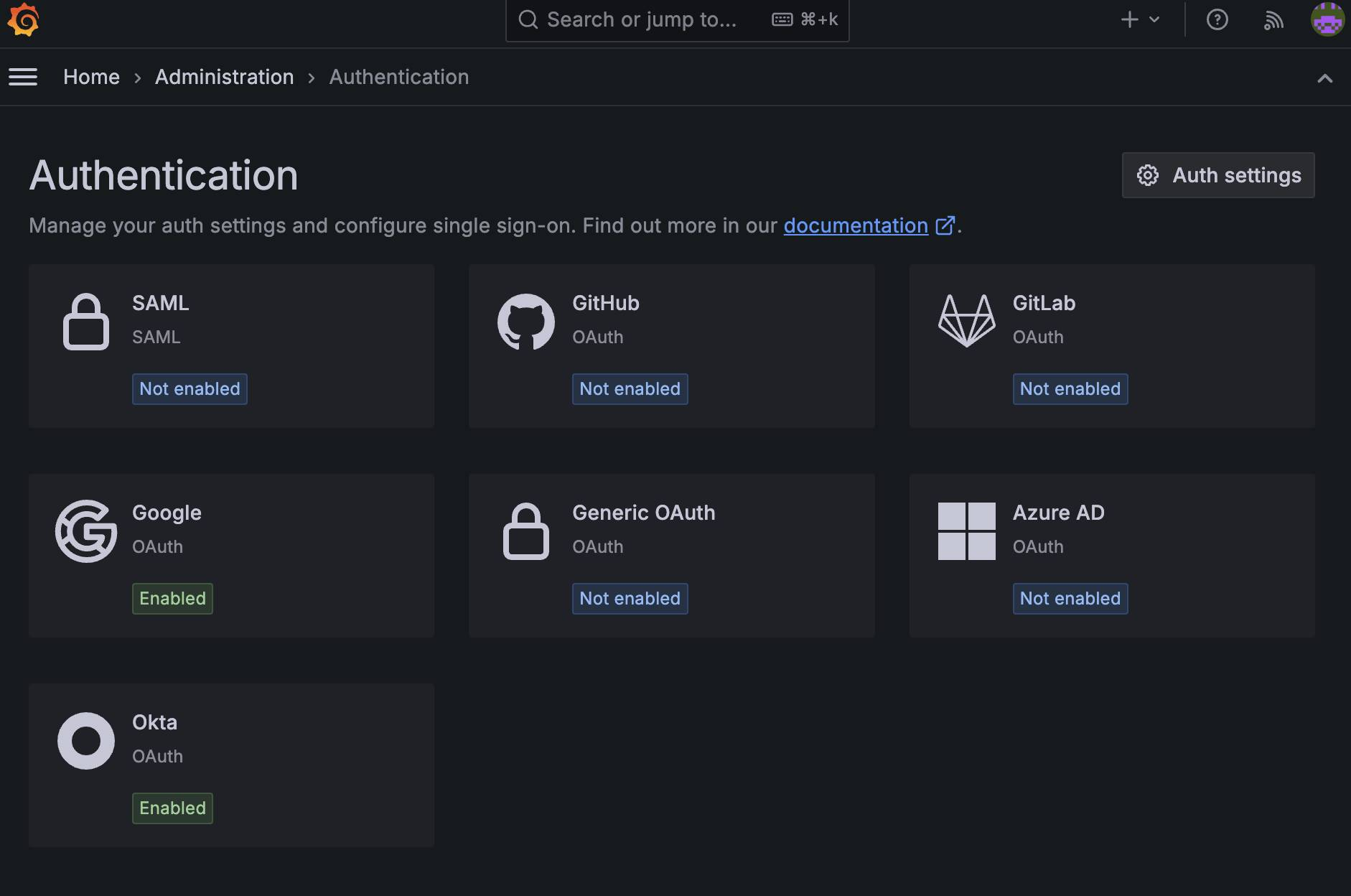
Exploring the Authentication user interface
To access the UI in Grafana or Grafana Cloud, navigate to Administration > Authentication in the navigation menu of your Grafana instance.
Please note that in order to access this page, a user must have the settings:read and settings:write permissions. By using the *settings:auth.{provider}:** scope with appropriate providers, you can control access by indicating which specific providers a user can set up.
Best practices to set up SSO
Setting up SSO requires knowledge of both identity providers and Grafana. With hundreds of identity providers available, offering built-in support for all of them is not feasible. This is why Grafana supports a Generic OAuth configuration, which can be used to set up SSO with any identity provider that supports OAuth 2.0.
Here are a few generic guidelines to follow when setting up SSO in Grafana:
- Understand your identity provider: Each IdP has specific requirements and quirks, so consult their documentation thoroughly before moving forward.
- Configure redirect Uniform Resource Identifier (URIs) correctly: Make sure the redirect URIs configured in your IdP match exactly with those specified in Grafana. Incorrect URIs can cause authentication failures.
- Avoid using Generic OAuth if your provider is supported by Grafana. If you are using Azure Active Directory, Okta, Google, GitHub or GitLab, use the appropriate configuration for them and avoid Generic OAuth. This approach simplifies setup and is less error-prone. Additionally, configuration is much more fine-grained, as certain functionality won’t be available with Generic OAuth.
- When using OAuth, configure allowed_domains, allowed_groups or allowed_organizations: This will reduce the attack surface for user accounts and create defense in depth (DiD) in case authentication is bypassed.
- Enable use_pkce=true for OAuth integrations: Proof Key for Code Exchange (PKCE) is an important addition to OAuth and it might be obligatory in future versions of the protocol. Enable it from the start to avoid breakage on IdP updates (it’s been enabled by default since Grafana 10.1).
- Use request signing when setting up SAML: Request signing is a critical security feature in SAML that enhances the overall security of the authentication process. It ensures SAML requests are genuine, unaltered, and originate from a trusted service provider, thereby protecting the system from various threats and ensuring compliance with security standards.
- Set up auto login: Available for OAuth and SAML, this will improve the user experience.
Troubleshooting SSO setup
Setting up SSO requires configuration in multiple places, and sometimes, it doesn’t work out the first time. Being prepared and having the right tools for debugging can streamline the process.
Be familiar with identity protocols
Most of the authentication protocols involve browser redirects and HTTP requests/responses between several components, so troubleshooting will be easier if you are familiar with the expected sequence of interaction for a particular scenario. Specifically, it will be helpful to know:
- The parameters expected by each protocol endpoint
- The responses and error codes returned by each endpoint
- The identity provider APIs
Tools to capture and view HTTP traces are especially helpful to troubleshoot during SSO setup. Most internet browsers offer dev tools with built-in capabilities to capture an HTTP trace in the “Network” tab. It is also convenient to be able to dump the HTTP trace to an HTTP Archive format (.har file), which will capture everything, including the cleartext value of any secret.
Other examples of tools for SSO debugging and troubleshooting include:
Know these debugging basics
When something is not working as expected, especially when it comes to authentication, it’s best to start checking the simple things. For example:
- Check that the identity provider is accessible and not experiencing any issues
- Ensure the supplied credentials are correct for the environment
- Check that the login account and credentials are not disabled or expired
- Make sure Grafana is using the correct URL for the identity provider
- Verify the client ID matches the one registered in identity provider
- Check the redirect/callback URL
- Read all error messages to see if they provide valuable clues
What’s next?
We hope the recent updates we’ve made related to the UI, API, and Terraform enhance your experience with Grafana and simplify the SSO setup process. Looking ahead, we plan to introduce a new UI and API for configuring LDAP, which will make authentication setup even easier.
In the meantime, if you want to learn more about how to organize your users and teams in Grafana to ensure optimal security, please refer to this blog post.
Grafana Cloud is the easiest way to get started with metrics, logs, traces, dashboards, and more. We have a generous forever-free tier and plans for every use case. Sign up for free now!
